Event
This page explains each element of the event data table and the details available in the event detail view.
MonitorDog Agent continuously monitors and records user behavior.
You can review and manage all event records from this page.
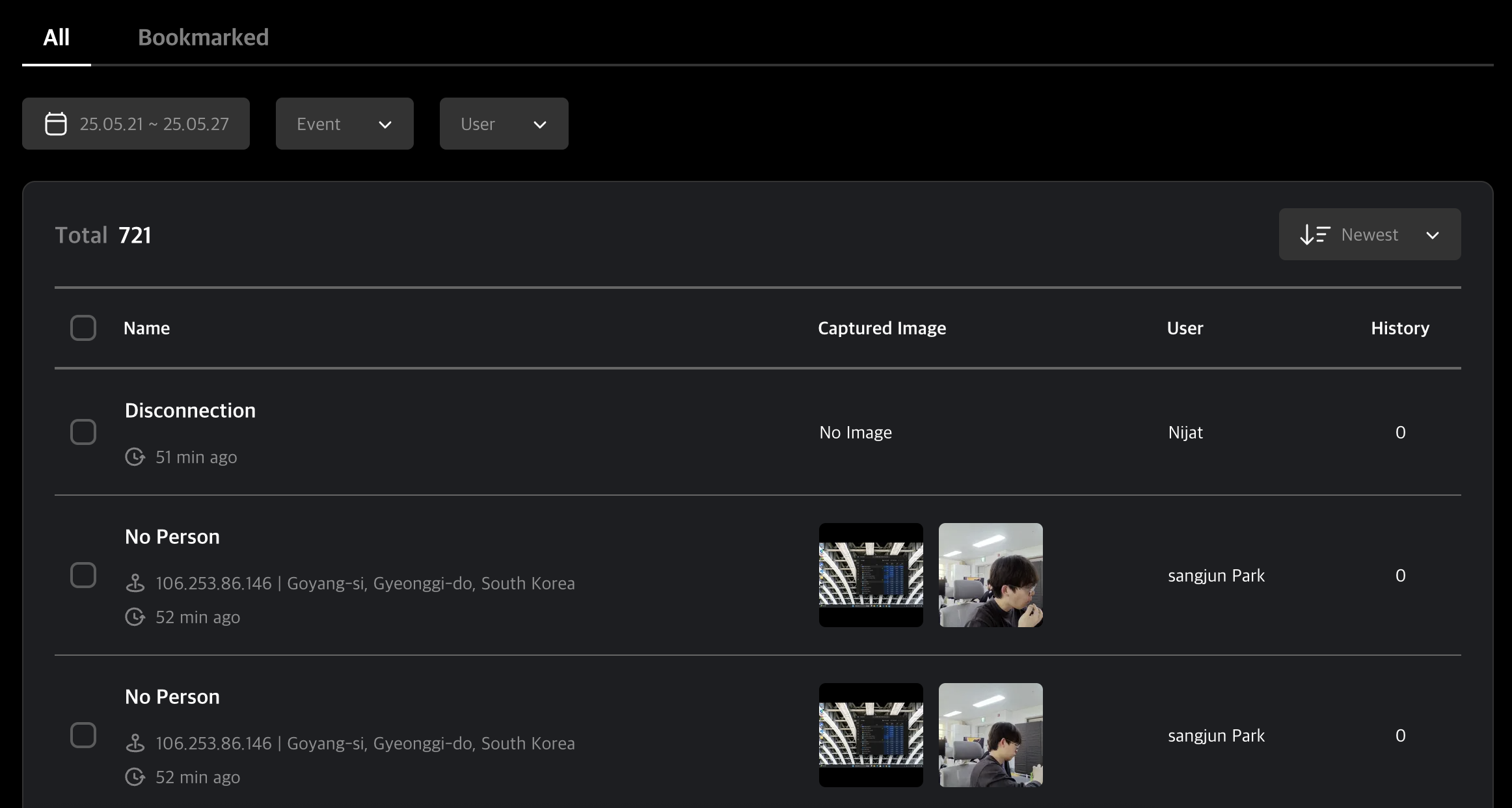
Data Table
You can browse the events detected by the MonitorDog Agent.
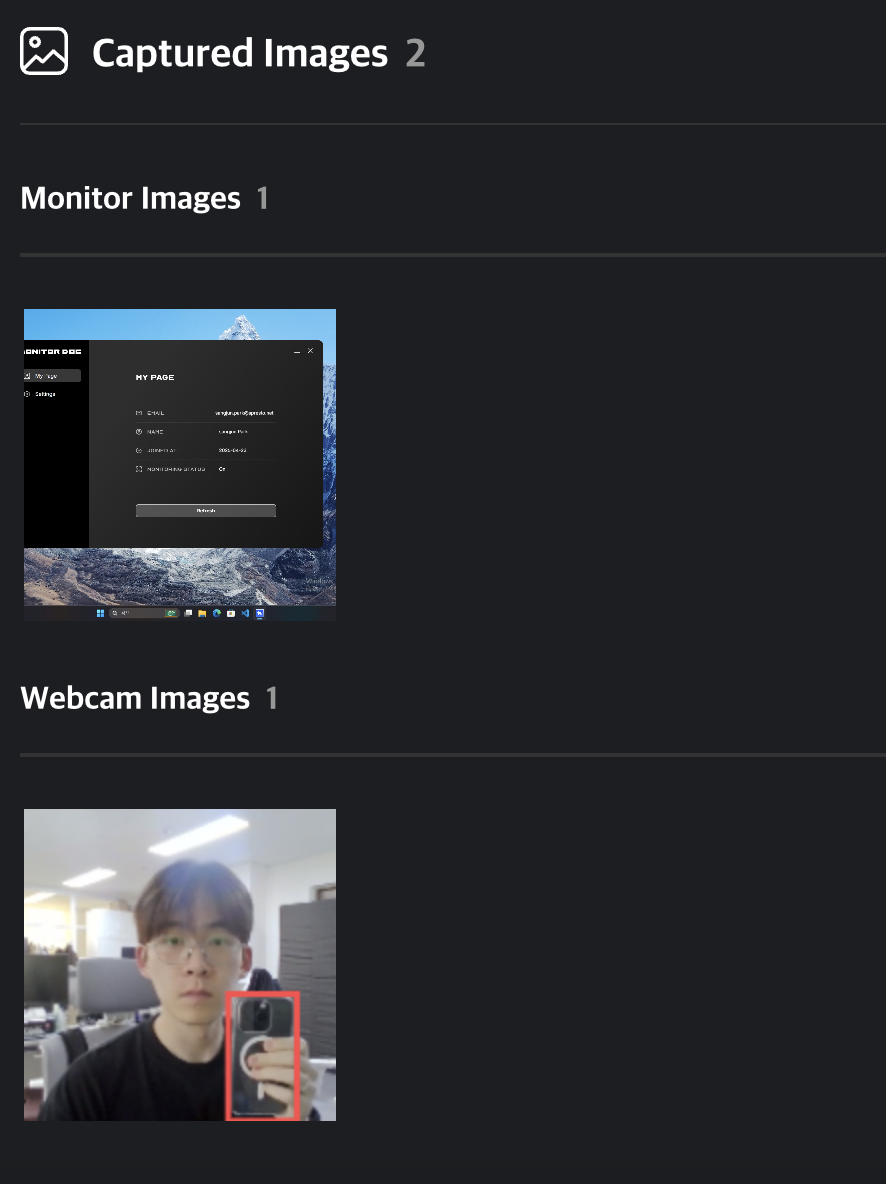
Each row includes one screen capture and one webcam image, along with brief event information.
Q. Why are some events missing images?
A. Not all events include screen or webcam images.
For example, webcam monitoring events include images, but events such as OS Reset or Disconnection (related to networking or system events) may not have any.
Table Tabs
Use the tabs at the top to filter events based on their suspicious activity status.
✅ Tab Descriptions
- All: View all event records.
- Bookmarked: View only bookmarked events.
Table Filters
Use the filters at the top of the table to narrow your search by date, event type, or user.
✅ Filter Features
- 📅 Date Range: Select a specific time period to view relevant events.
- ⚠️ Event: Filter the table by specific event types detected by the Agent.
- 🔍 Search Users: Search and view events by specific users.
Event Detail Page
Clicking an event opens the detail view where you can see full information and share the event with other admins.
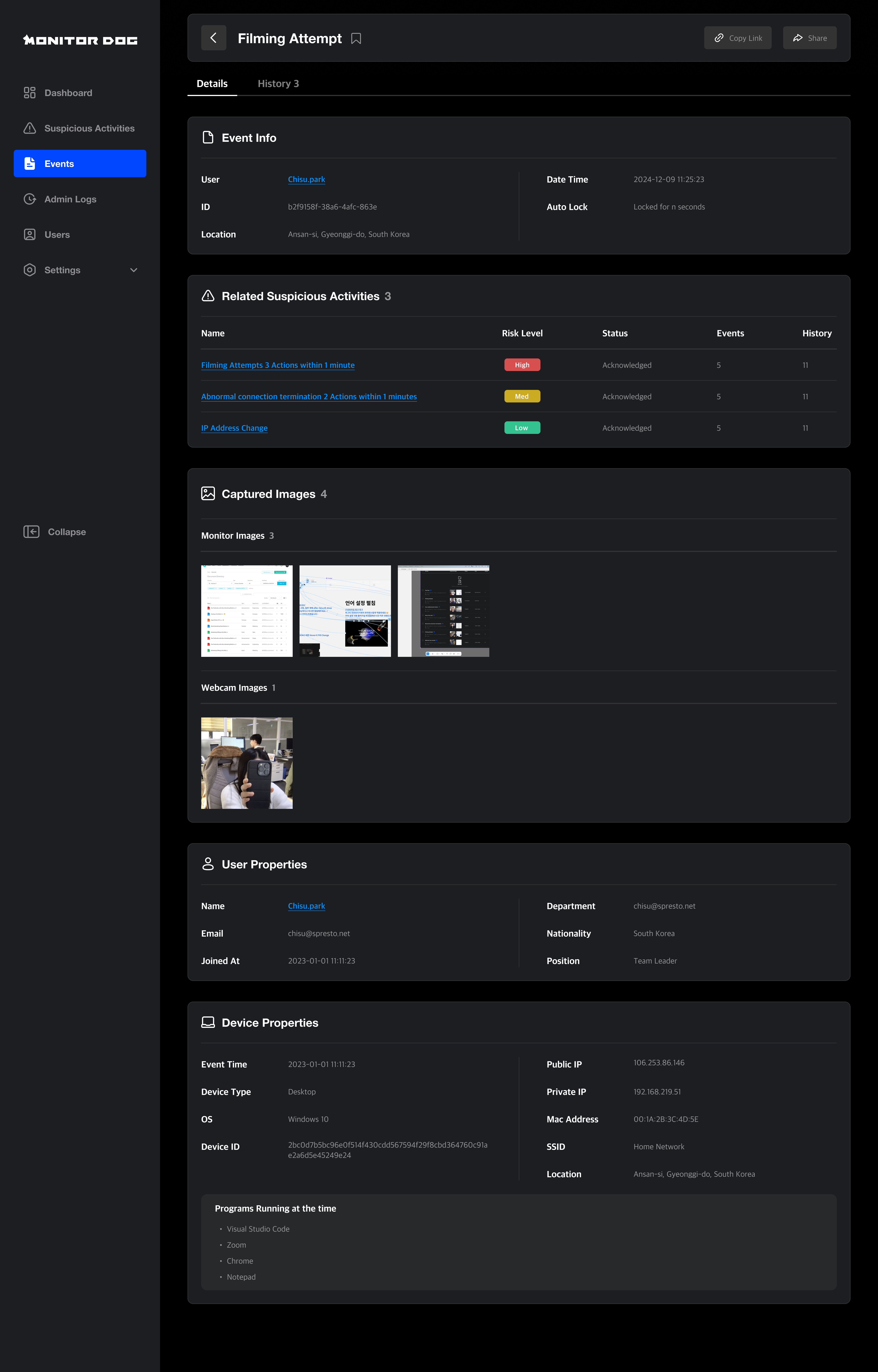
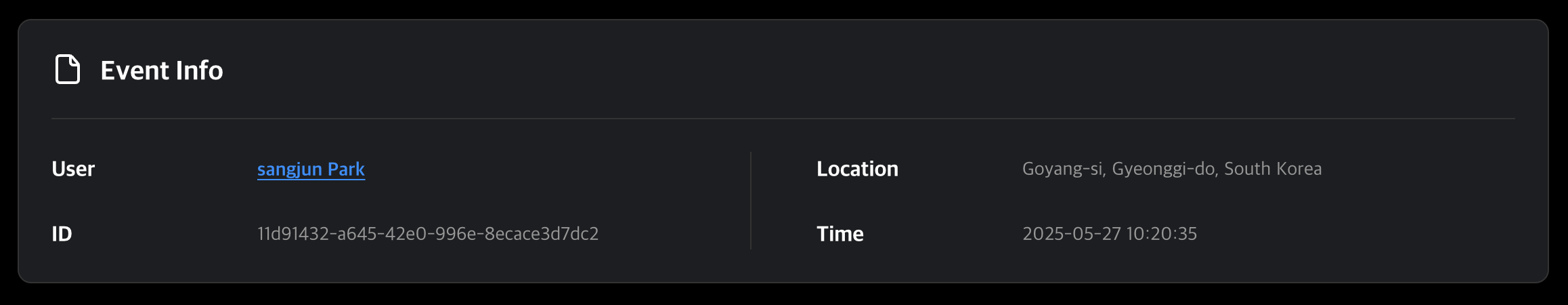
Event Info
Displays the user’s name, location of the event, timestamp, and event ID.
Clicking the user’s name takes you to their User Detail Page.
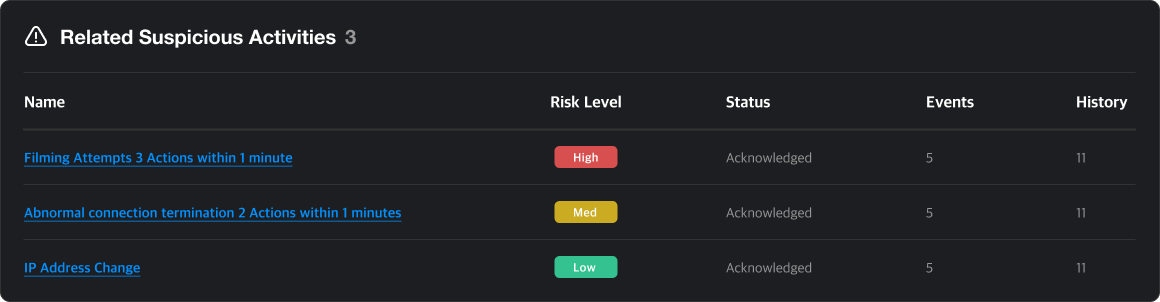
Recent Suspicious Activity
If the event is part of a suspicious activity, you will see its name, risk level, review status, number of related events, and history count.
Clicking the suspicious activity takes you to the Suspicious Activity Detail Page.
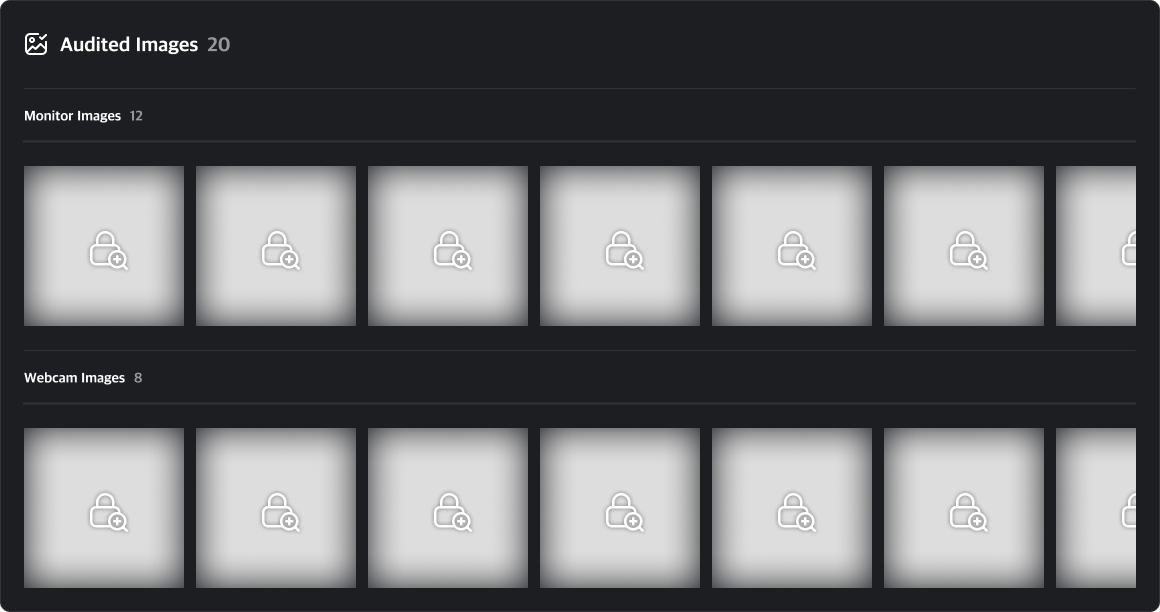
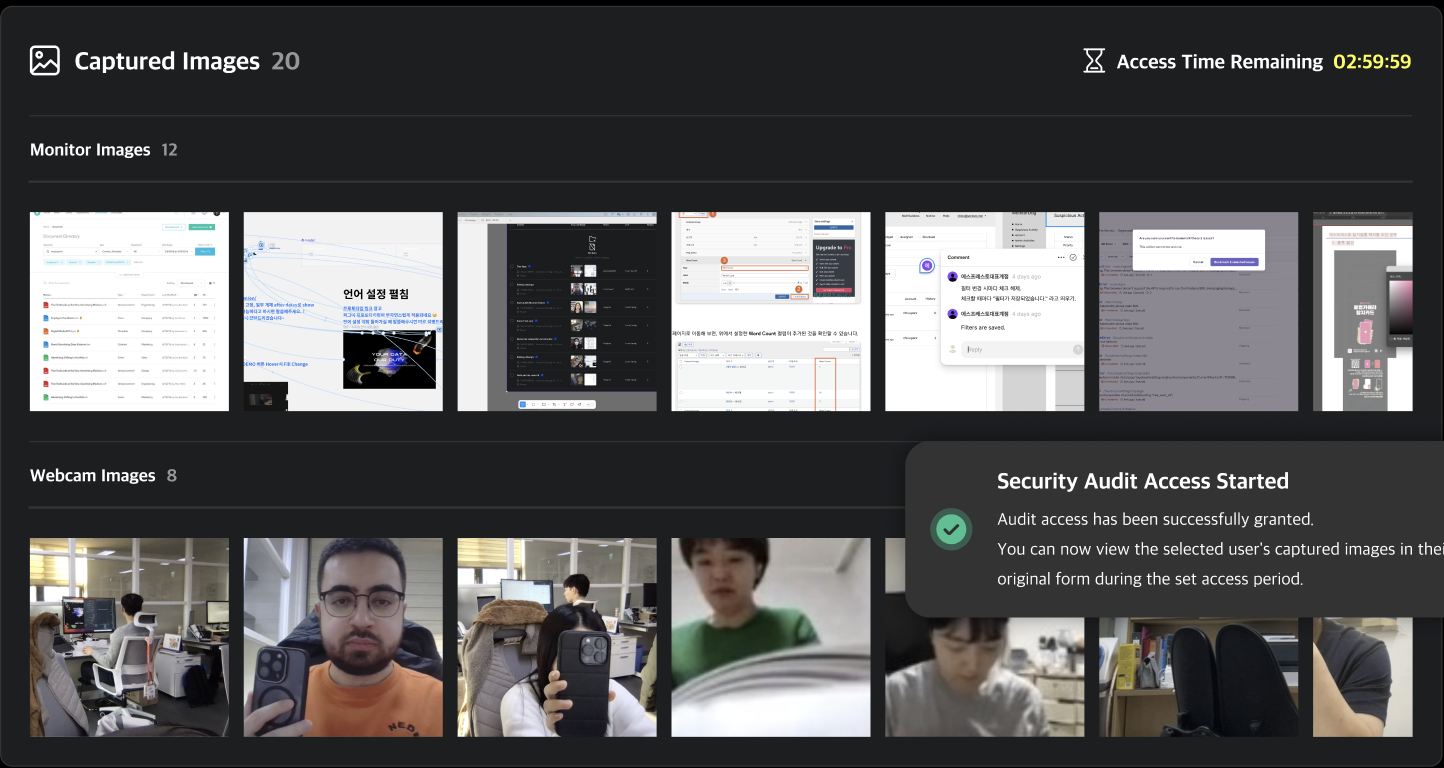
Event Images
You can view screenshots and webcam images captured at the time of an event. By default, all images are set to private. To view these images, you must submit a Security Audit request.
Clicking on a private image will open a security audit request modal. You can start a security audit by entering the target period and audit time along with the reason for the request.
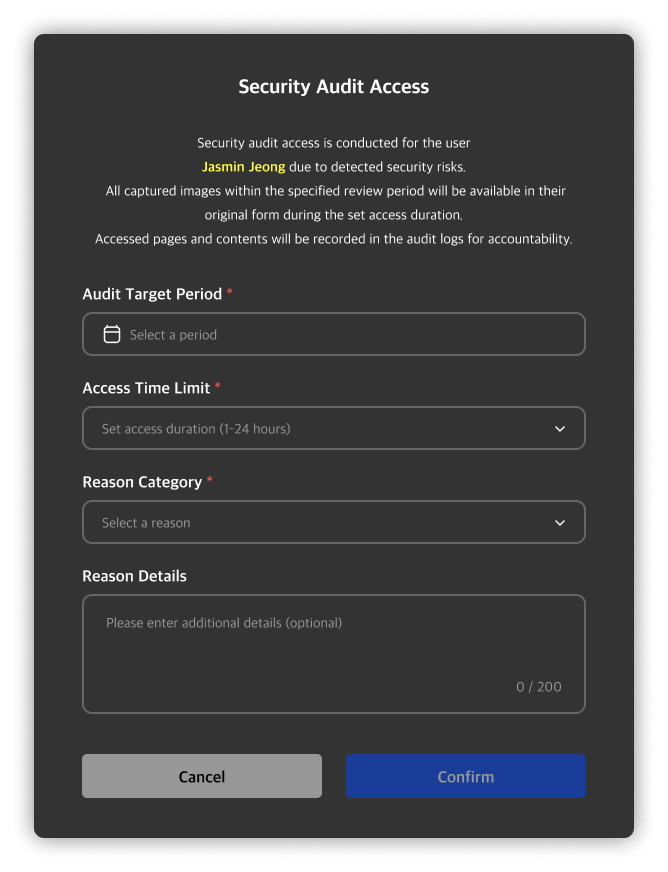
Once the audit begins, a countdown timer will appear at the top right based on the configured audit time, and the images will be made accessible. Any image viewed from the event detail page will be added to the security audit list, and you can review the events and images later via the security audit detail page.
Q. I can’t submit an audit request!
A. Only administrators with Viewer or higher permissions can submit a security audit request. If you want to view the images and proceed with the audit, please contact a higher-level administrator to request a permission change.
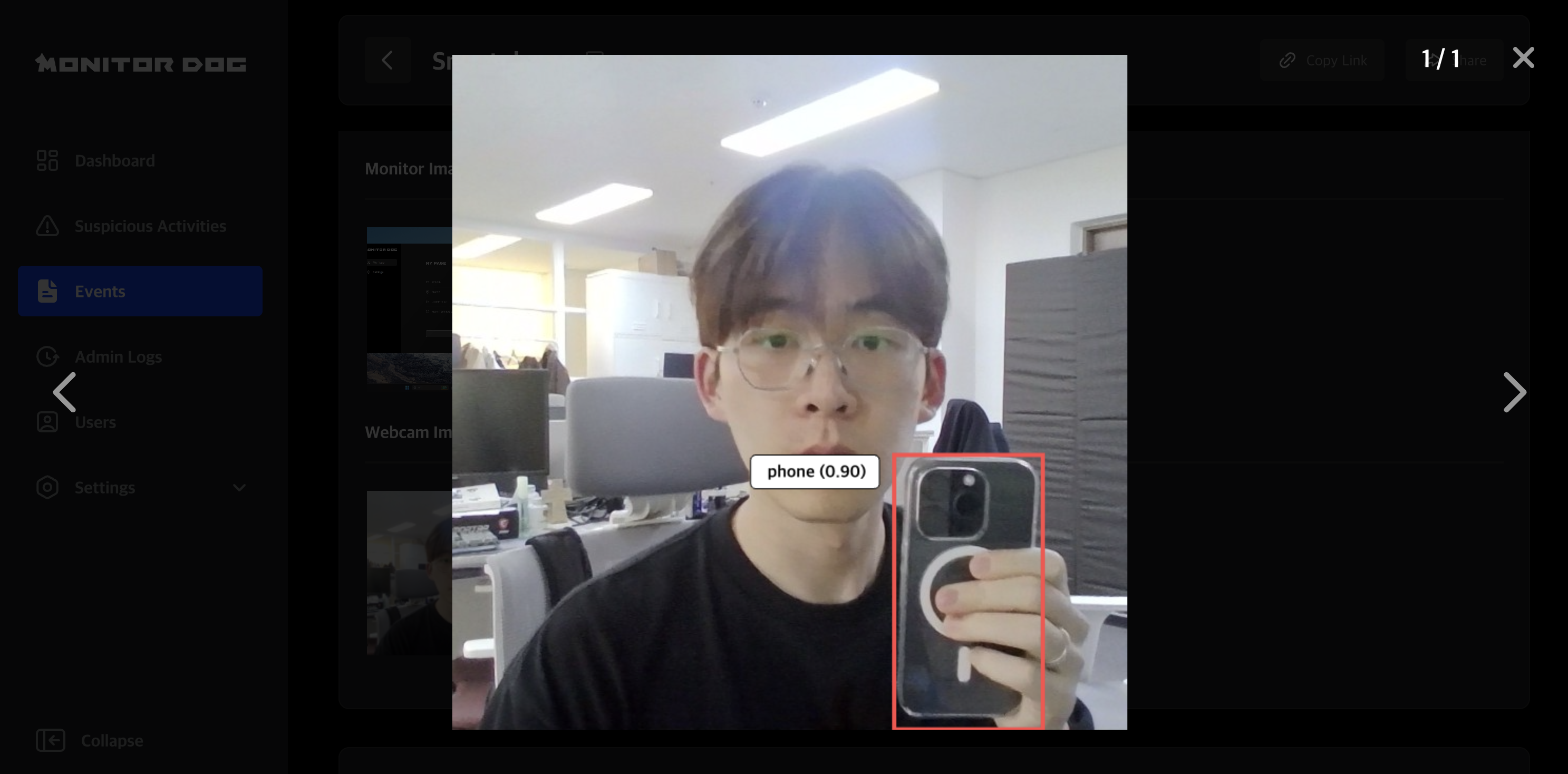
Smartphone Detection Events
In smartphone detection events, the webcam image highlights the detected phone.
MonitorDog's AI model automatically detects and marks the location of the phone.
Click the image to enlarge and view the detection with risk score and precise position.
User Info
Shows details about the user involved in the event.
Clicking the user’s name navigates to their detail page.
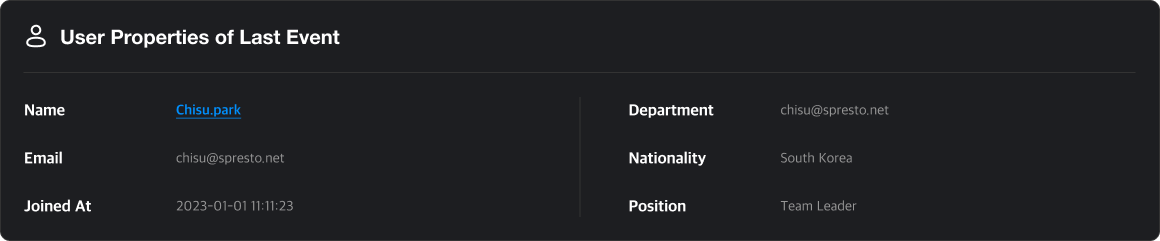
Q. How can I add information that wasn't filled in during signup?
A. Fields like Department and Nationality cannot be edited by users.
These can only be added or modified by administrators (Editor role or higher).
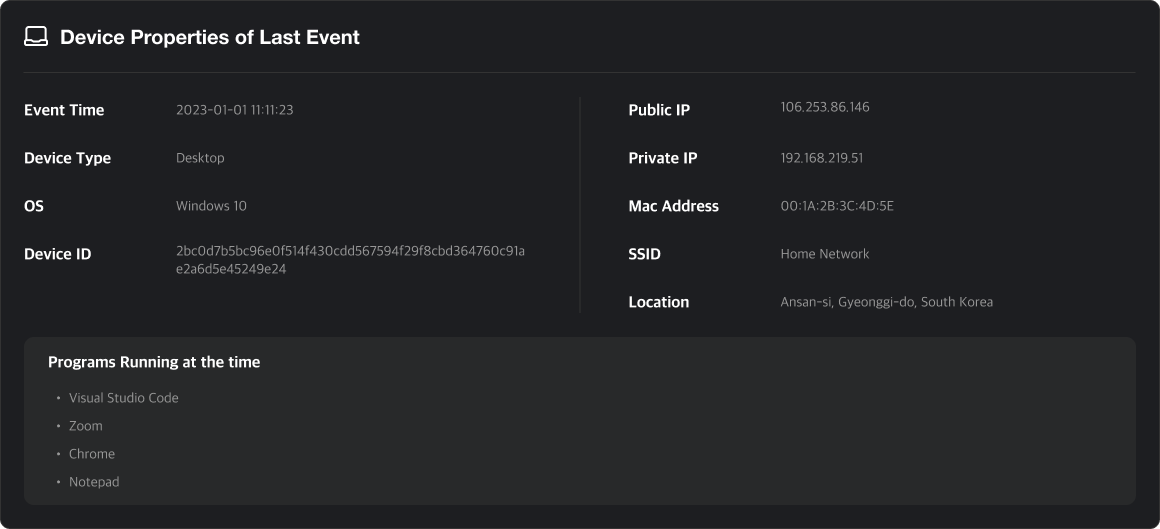
Device Info
Displays device information and a list of running programs at the time of the event.
This data is collected by the MonitorDog Agent.
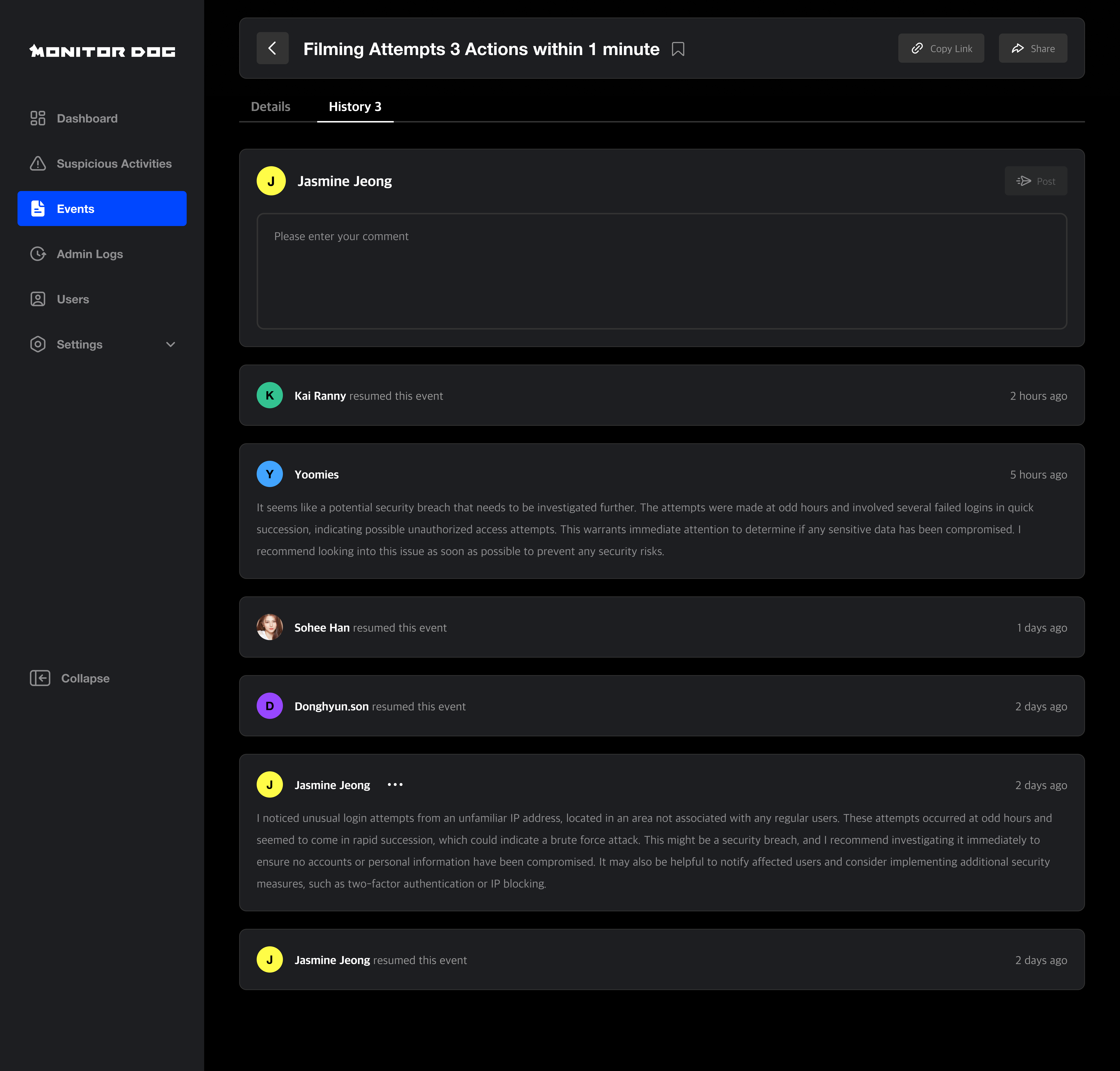
History
Logs key actions related to the event. You can review all administrative actions and comments left here.
Q. When is history created?
A. History is generated when:
- An admin updates the review status or risk level
- A suspicious activity is shared with another admin
- An admin leaves a comment to provide context or guidance
Sharing
There are two ways to share an event or suspicious activity:
- Copy Link: Useful for sharing outside the system.
- Direct Share: Share with specific admins within MonitorDog.
You can share with multiple users at once. This action is logged in the history and generates a notification for recipients.