Detection Scenarios
This page provides an overview of the Detection Scenario management features in the MonitorDog Admin Console.
You can create and manage scenarios that define how suspicious behaviors are detected.
Scenario Table
View a list of configured scenarios, grouped by type.
Click on a scenario to view its detailed settings.
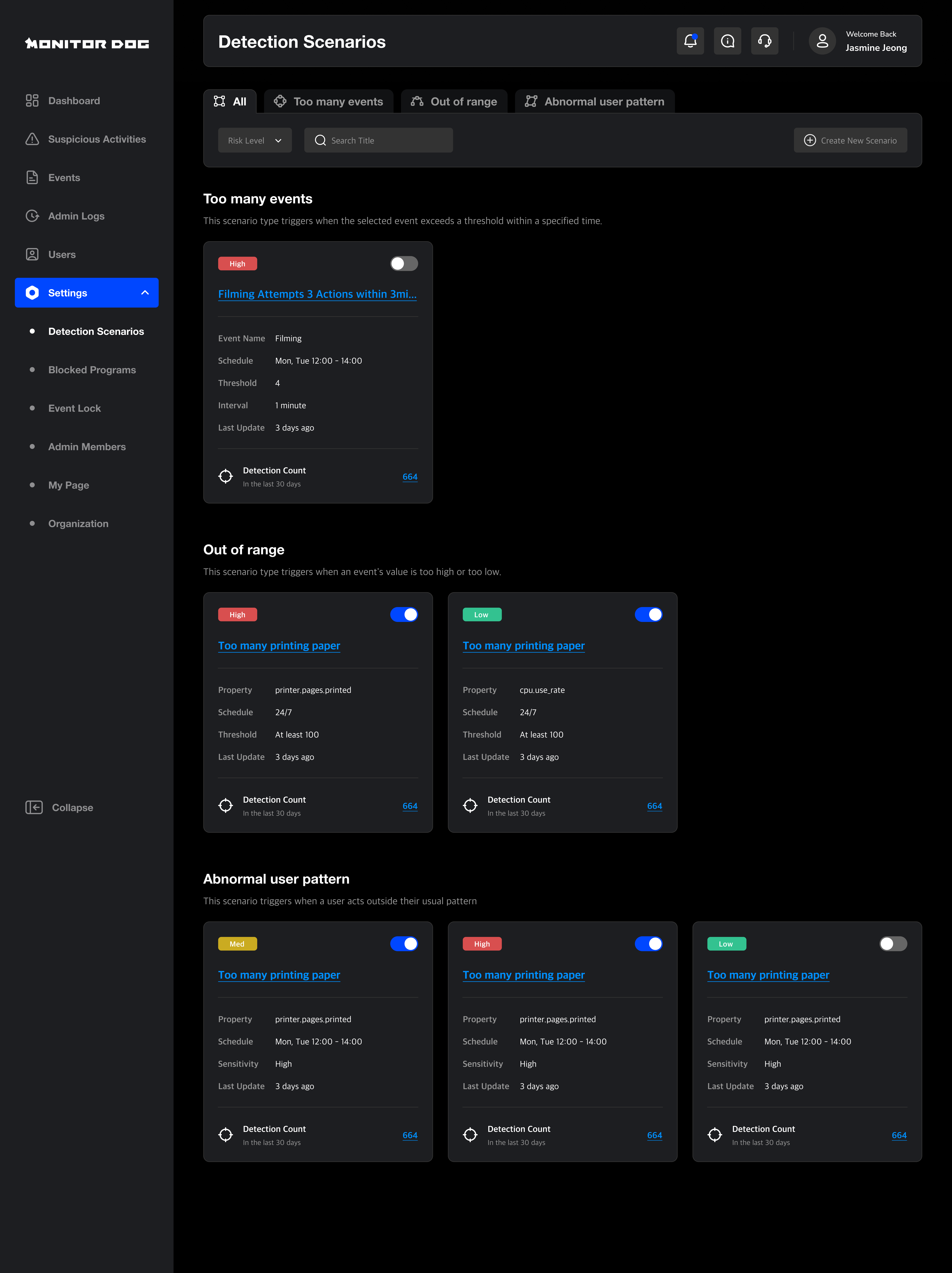
Table Filtering
- Use the top tab to filter by scenario type.
- Filter by Risk Level.
- Search for scenarios by name.
Scenario Card
Each scenario card provides a quick overview and toggle switch to enable or disable the scenario.
Q. The toggle doesn’t work!
A. Only administrators with Editor or higher permissions can modify scenario status.
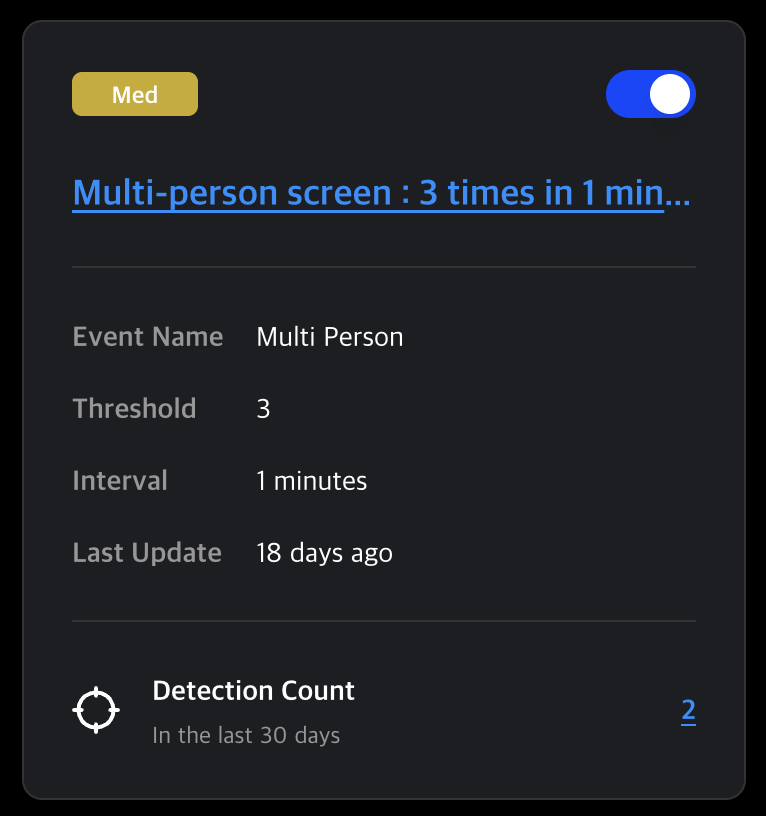
Card Details
- Toggle Button: Enables or disables the scenario. Only enabled scenarios are actively monitored.
- Event Name: The event type used to trigger the scenario.
- Threshold: Sensitivity level (1–100).
- Interval: Detection interval (1 minute to 1 year).
- Last Update: Date of last modification.
- Detection Count: Number of detections in the past month.
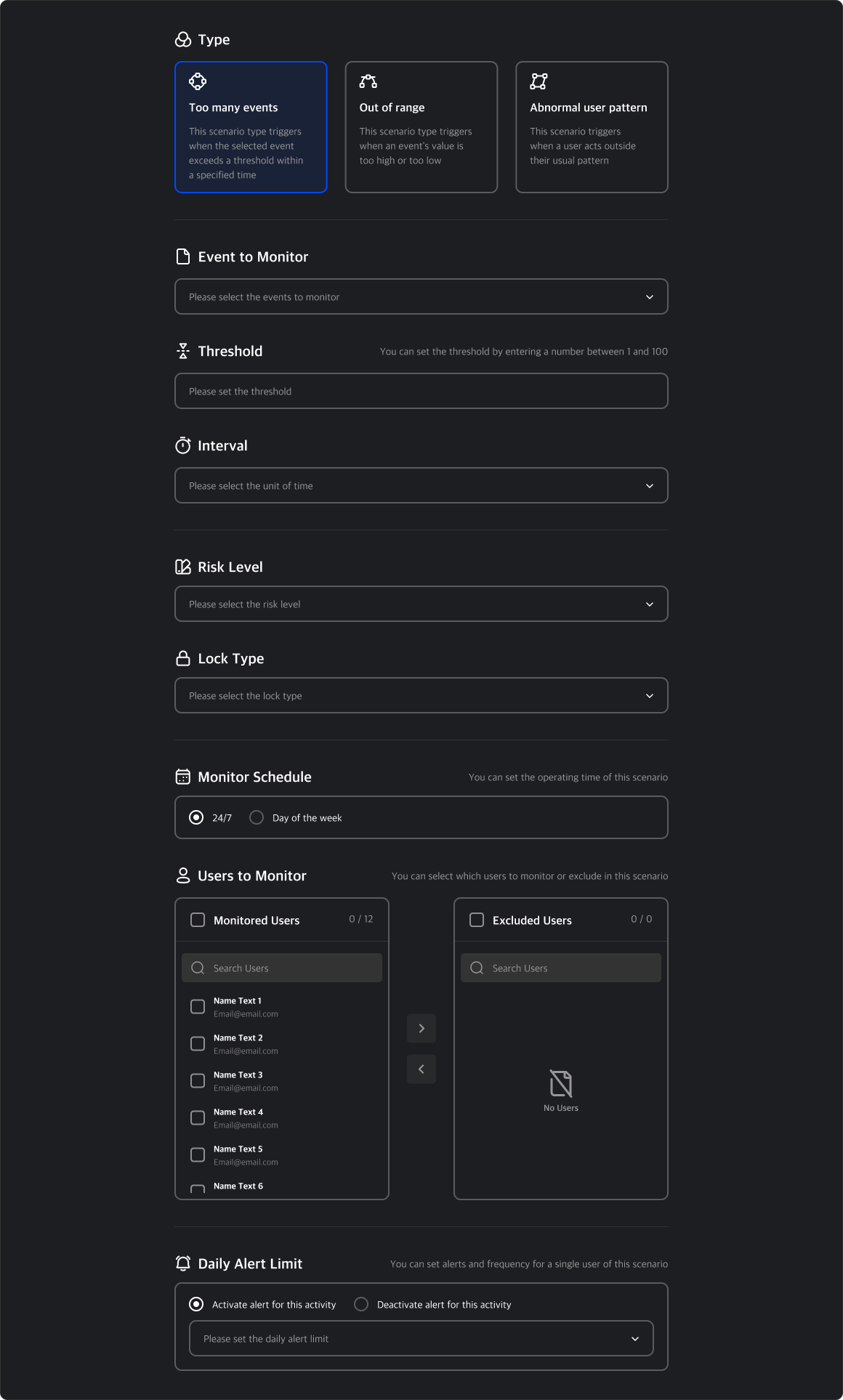
Create Scenario
Click the “Create Scenario” button to configure a new detection scenario.
Three scenario types are available depending on your monitoring needs.
⚠️ Only administrators with Editor or higher permissions can create scenarios.
- Too many events: Triggers when a specific event occurs multiple times within a given interval.
- Out of range: Triggers when a metric is above or below a certain threshold.
- Abnormal user pattern: Triggers when user behavior deviates from normal patterns.
Too many events
Triggers when a selected event occurs a specified number of times within a time window.
For example: “If the No Person event is triggered 3 times in 1 minute, lock the user’s device.”
-
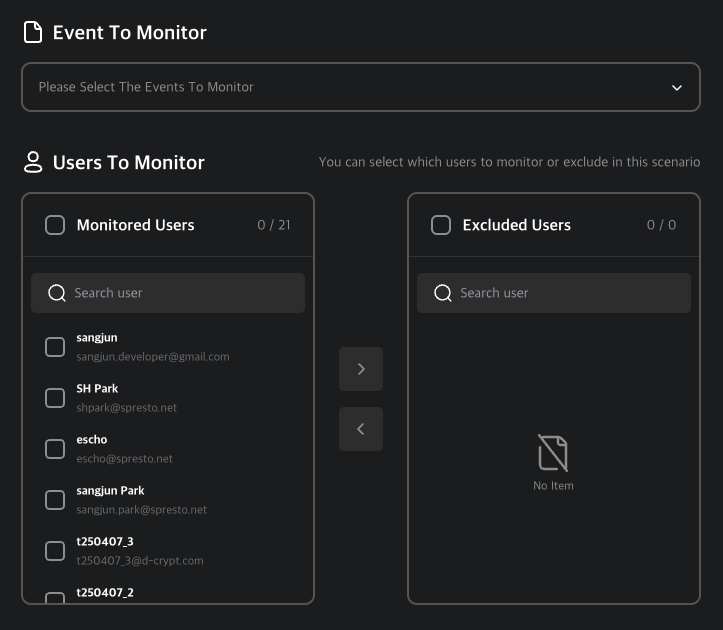
Select Events and Users
Choose the events and users to monitor.
Supported Events
- Smartphone
- Logout
- Exit
- Login
- Multi person
- No person
- Disconnection
- OS Shutdown
- OS Lock
- Is Sleep
-
Sensitivity and Interval
Configure how sensitive the scenario is and how often events are measured.
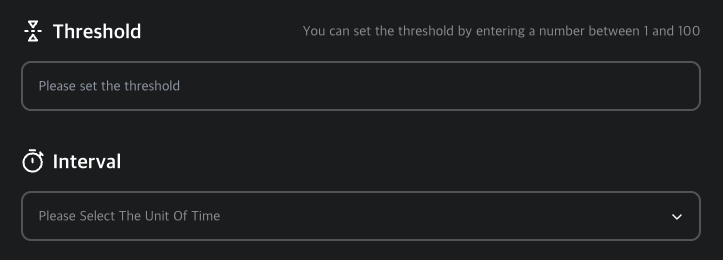
- Threshold: Value from 1 to 100.
- Interval: Value from 1 minute to 11 years.
Out of range
Triggers when a metric falls outside a specified range.
For example: “If CPU usage is greater than 90% or less than 10%, lock the user’s device.”
-
Select Events and Users
Choose the resource metric and the users to monitor.
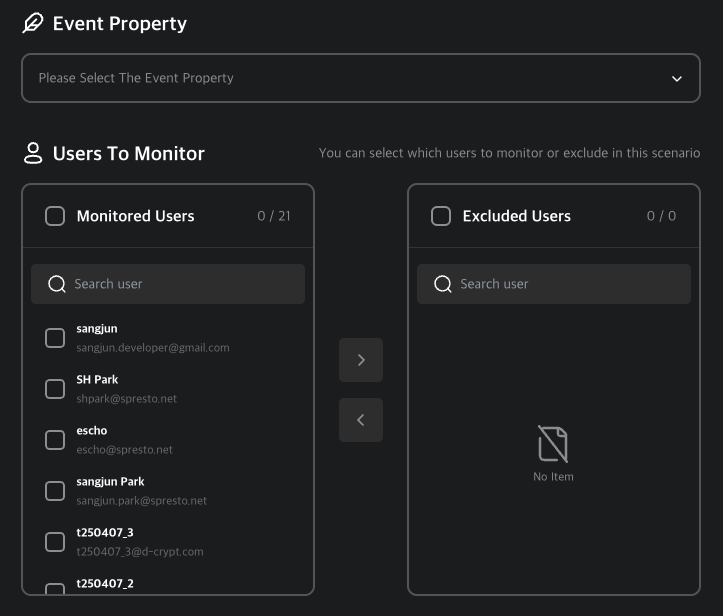
Supported Metrics
- CPU Use Rate
- Memory Use Rate
-
Sensitivity Settings
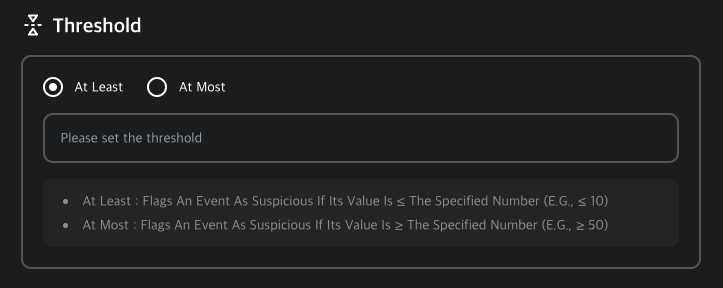
- At Least: Trigger if value is below a specified minimum.
- At Most: Trigger if value is above a specified maximum.
Abnormal user pattern
Triggers when user activity deviates from normal patterns.
For example: “If a user logs in from an unusual IP address, lock the device.”
-
Select Events and Users
Choose the event type and users to monitor.
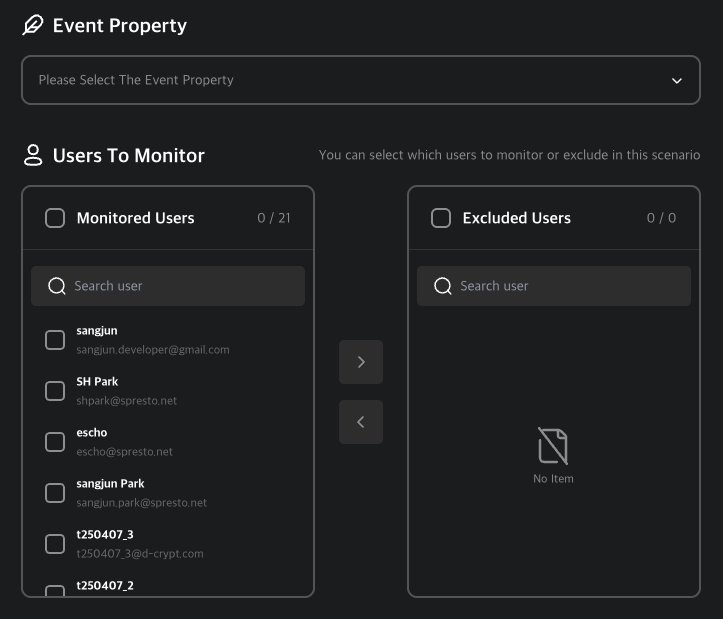
Supported Events
- Unusual IP
- OS Reset
- Disconnection
Common Settings for All Scenarios
These settings apply to all scenario types:
-
Risk Level & Lock Type
Set the Risk Level and Lock Type to be applied when the scenario is triggered.
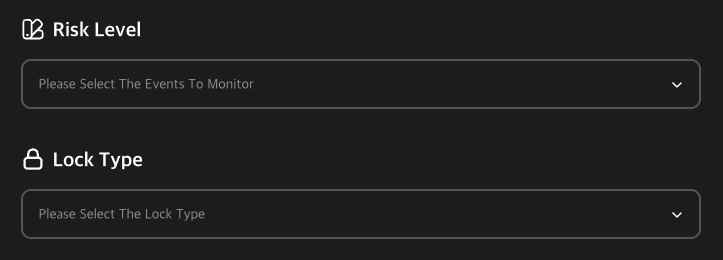
Lock Type Options
- None: No lock will be applied.
- User-Controlled: Users can unlock the device themselves.
- Admin Approval Needed: Admin must manually approve unlock requests.
-
Title and Description
Give your scenario a name and (optionally) a description.
The scenario name will also be shown as the title for suspicious activity entries.
Q. Are all fields required?
A. All fields except for the description must be filled in to activate the “Create” button.
We recommend providing a description for clarity.