Suspicious Activity
This page explains the elements of the suspicious activity data table and the details available on each suspicious activity page.
Suspicious activities are generated based on events detected by the MonitorDog Agent and can be reviewed or edited from this page.
Data Table
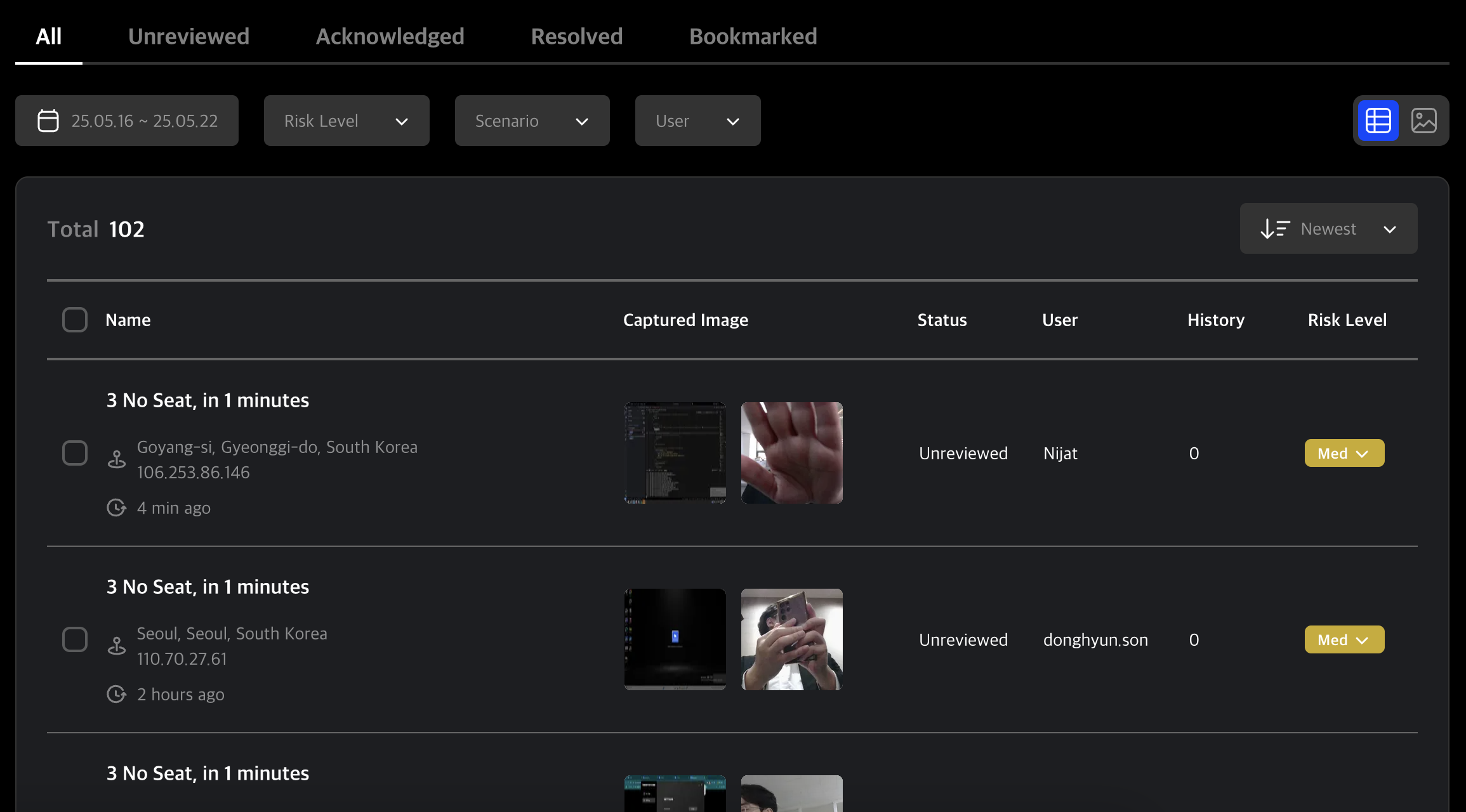
You can view a list of suspicious activities triggered by scenarios.
Each record includes a screen capture and webcam image, as well as brief information about the activity.
Risk Levels
- High: High-risk suspicious behavior
- Med: Medium-risk behavior
- Low: Low-risk behavior
Q. How are risk levels assigned to suspicious activities?
A. Risk levels are set by administrators when creating scenarios.
When the scenario is triggered, the associated risk level is applied to the suspicious activity.
Admins with Editor permission or higher can modify the risk level.
See more in the Scenario Creation Page.
Q. Why do some activities not include images?
A. Not all events include webcam and screen images.
Webcam-monitoring events will include images, but system/network-based events like OS Reset or Disconnection may not.
Q. The same scenario is still being triggered, but no new suspicious activity is generated!
A. A new suspicious activity is created the first time a scenario is triggered.
If the same event and scenario repeat within 5 minutes, they are merged into the original activity.
After 5 minutes, a new instance will be created as a separate suspicious activity.
Table Tabs
Use the top tabs to filter data by review status.
✅ Tab Descriptions
- All: View all suspicious activities
- Unreviewed: Unreviewed items
- Acknowledged: Marked as acknowledged by an admin
- Resolved: Marked as resolved by an admin
- Bookmarked: Items bookmarked by users
Table Filters
You can filter suspicious activities by date, risk level, scenario, and user.
✅ Filter Features
- 📅 Date Range: View records within a specific time frame
- ⚠️ Risk Level: Filter by severity
- 🧩 Scenario: Filter by specific scenario types
- 🔍 Search Users: Filter data by user
Image View Mode
Click the image icon in the top-right corner to switch to Grid View for quick image browsing.
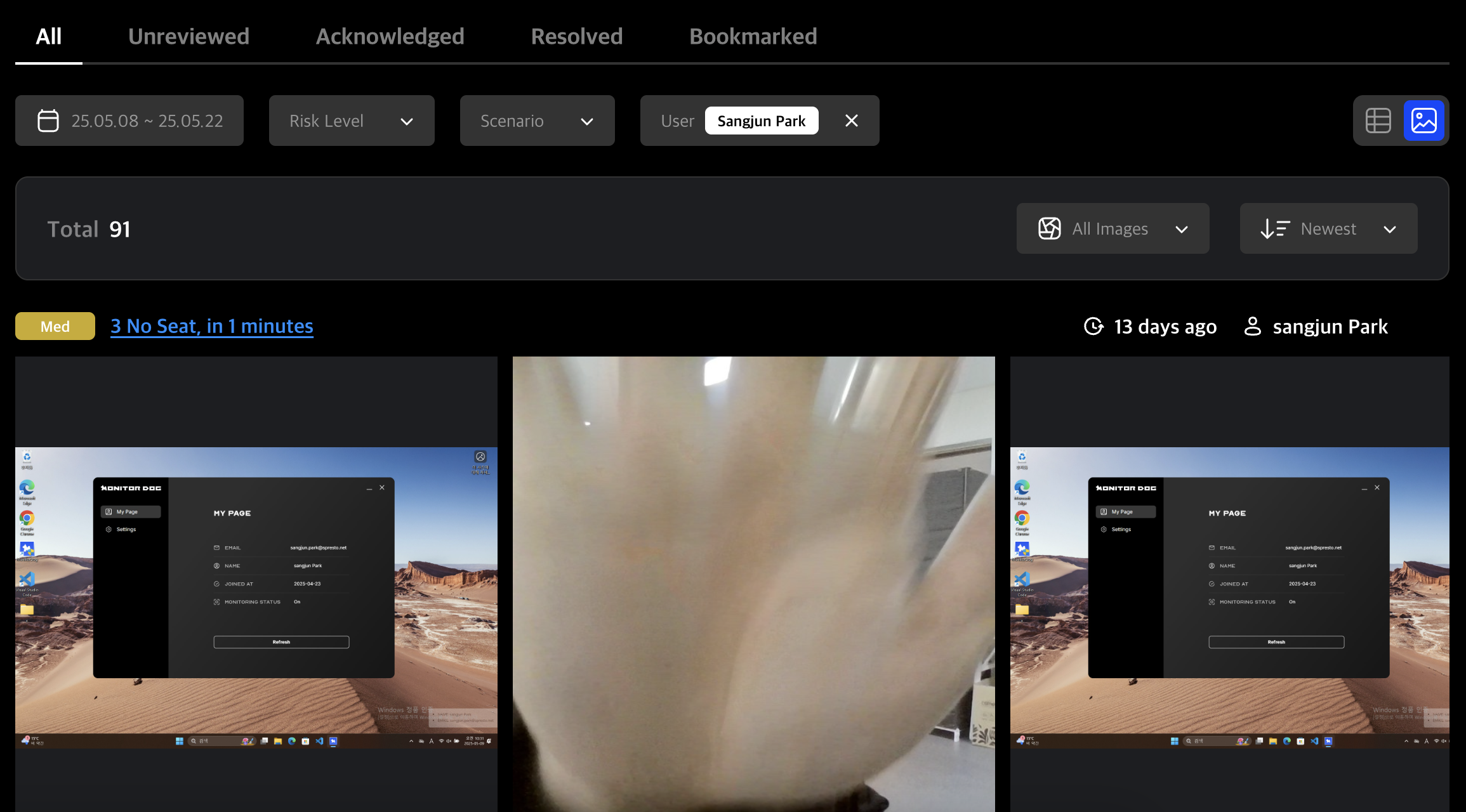
This grid alternates between webcam and screen captures. Click an image to view it in fullscreen slider mode.
✅ Image Type Selector
Use the All Images dropdown to toggle between all, screen-only, or webcam-only images.
Table Data
Each entry includes the suspicious activity name, location, timestamp, and user.
If applicable, it also includes screen and webcam captures.
Additional data includes review status, history logs, and risk level.
Q. Why can’t I change the risk level?
A. Only admins with Editor permission or higher can modify the risk level.
Q. The timestamps don’t match my local time!
A. You can update your timezone in the My Info page.
If the issue persists, ask your organization admin to check the org-wide timezone settings.
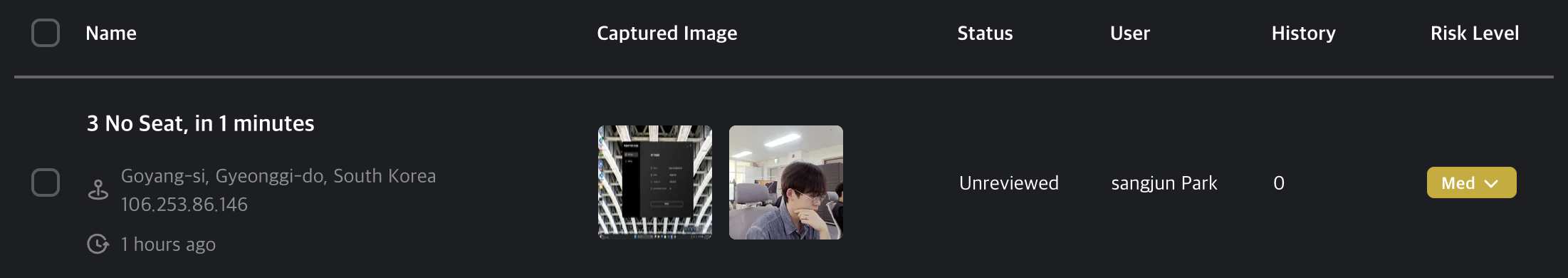
Use the checkboxes to select one or multiple suspicious activities.
Then you can change review status, adjust risk level, or bookmark the selected items.
Q. I only see the bookmark option when I select items!
A. Risk level and review status actions are only available to Editors or higher.
Suspicious Activity Detail Page
Clicking on a suspicious activity opens its detail page.
You can view full details, update its status, or share the item with other admins.
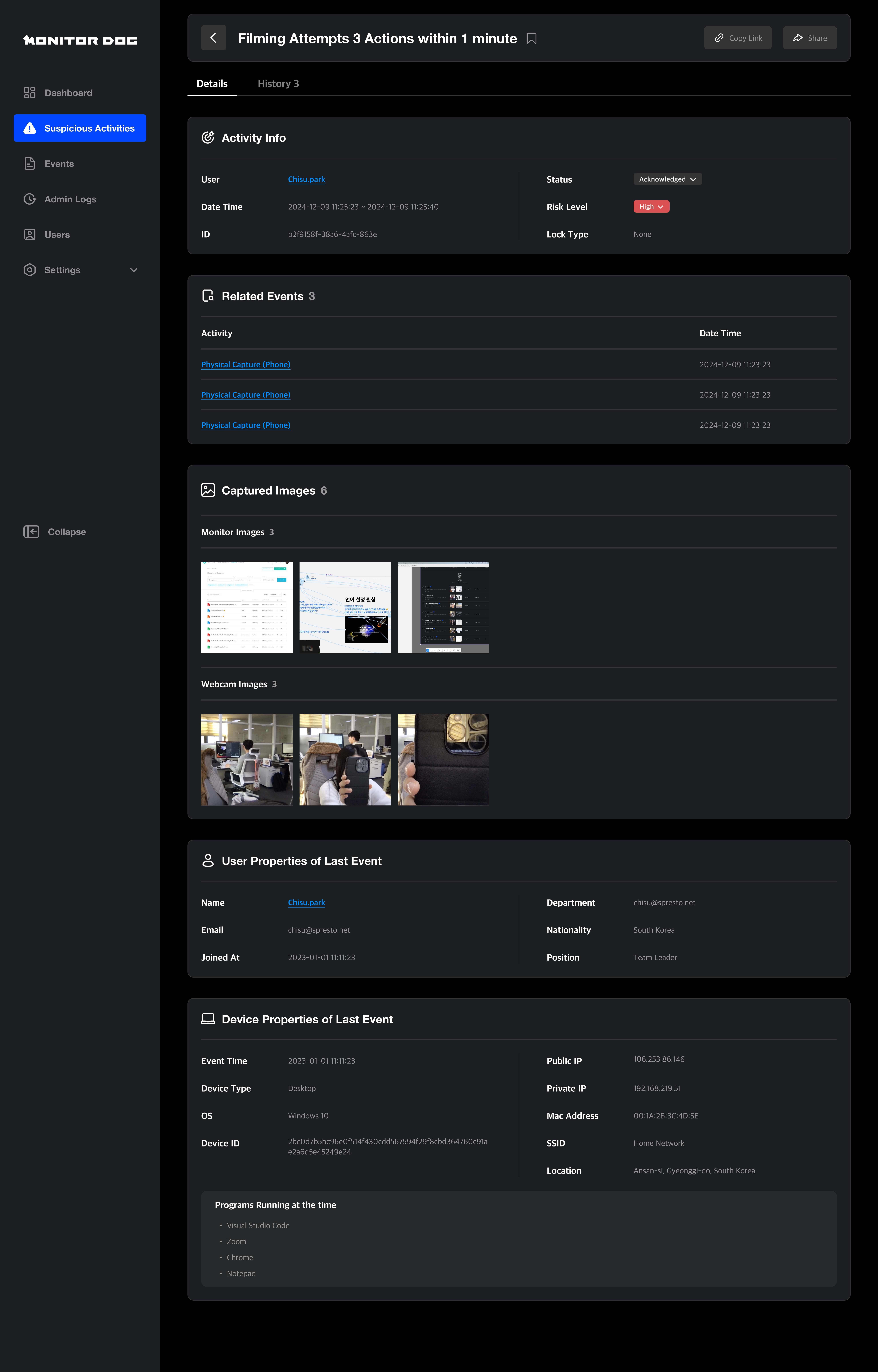
Suspicious Activity Info
Displays comprehensive information about the selected suspicious activity.
You can modify the review status and risk level.
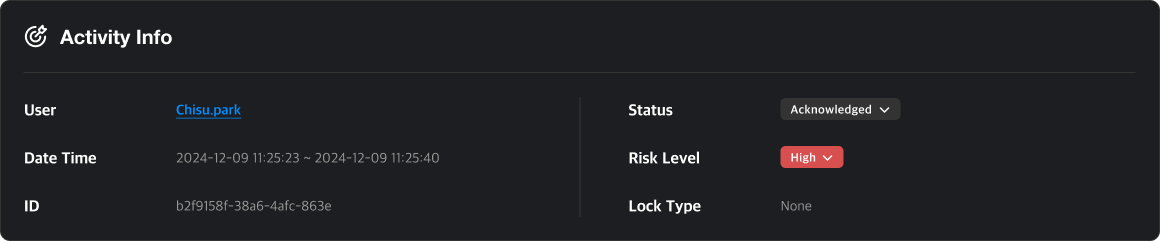
Review Status Guide
- Unreviewed: Default status, not yet reviewed
- Acknowledged: Identified and under review
- Resolved: Marked as addressed
Q. I viewed the activity, but the review status didn’t change!
A. Simply viewing does not update the review status.
You must manually change the status after review. Editor-level access or higher is required.
Related Events
View the events associated with this suspicious activity.
Each shows its name and time. Click to view the event detail page.
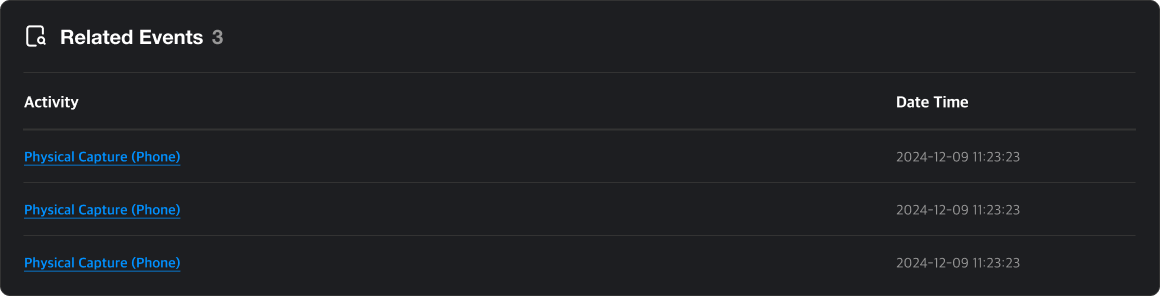
Q. Why are there events listed in this suspicious activity?
A. Suspicious activities are generated based on scenarios tied to specific events.
The related events are displayed within each activity. See Scenario and Suspicious Activity in the glossary.
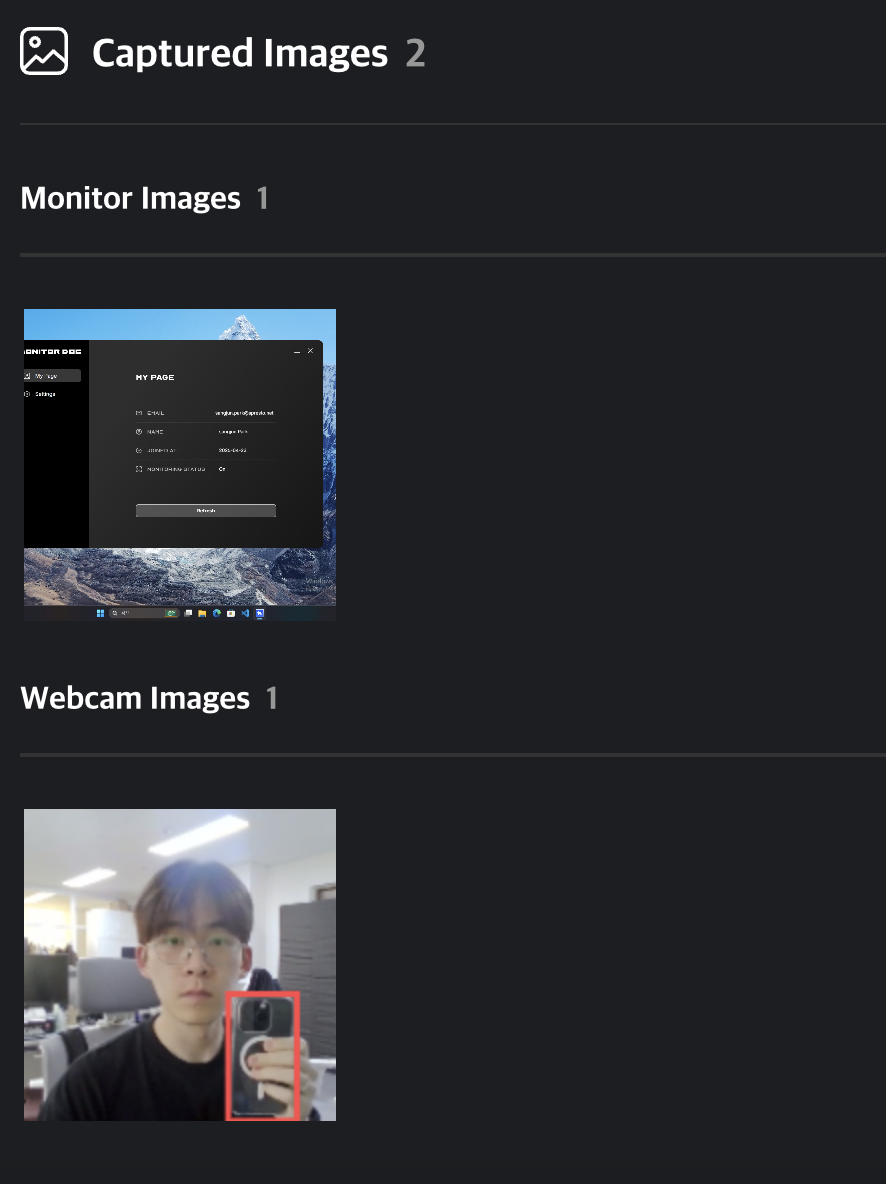
Event Images
You can view screenshots and webcam images captured at the time of an event. By default, all images are set to private. To view these images, you must submit a Security Audit request.
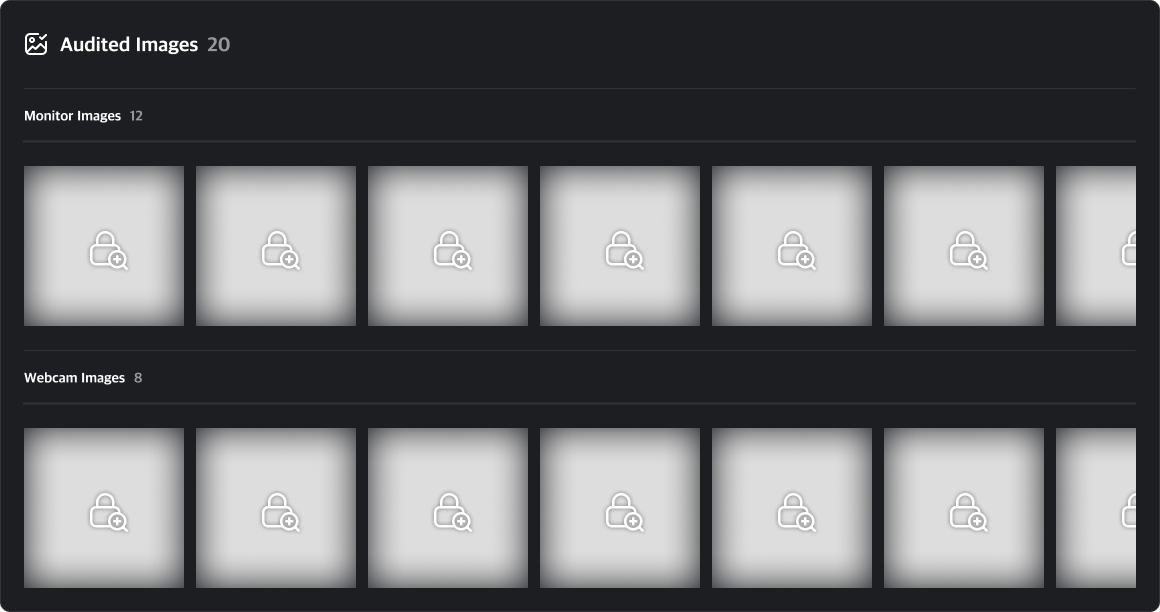
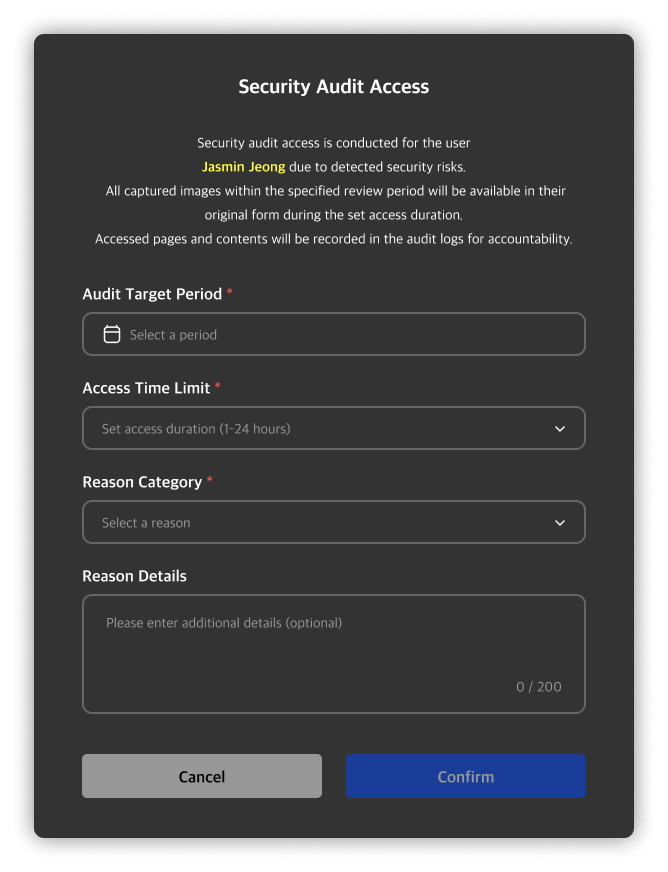
Clicking on a private image will open a security audit request modal. You can start a security audit by entering the target period and audit time along with the reason for the request.
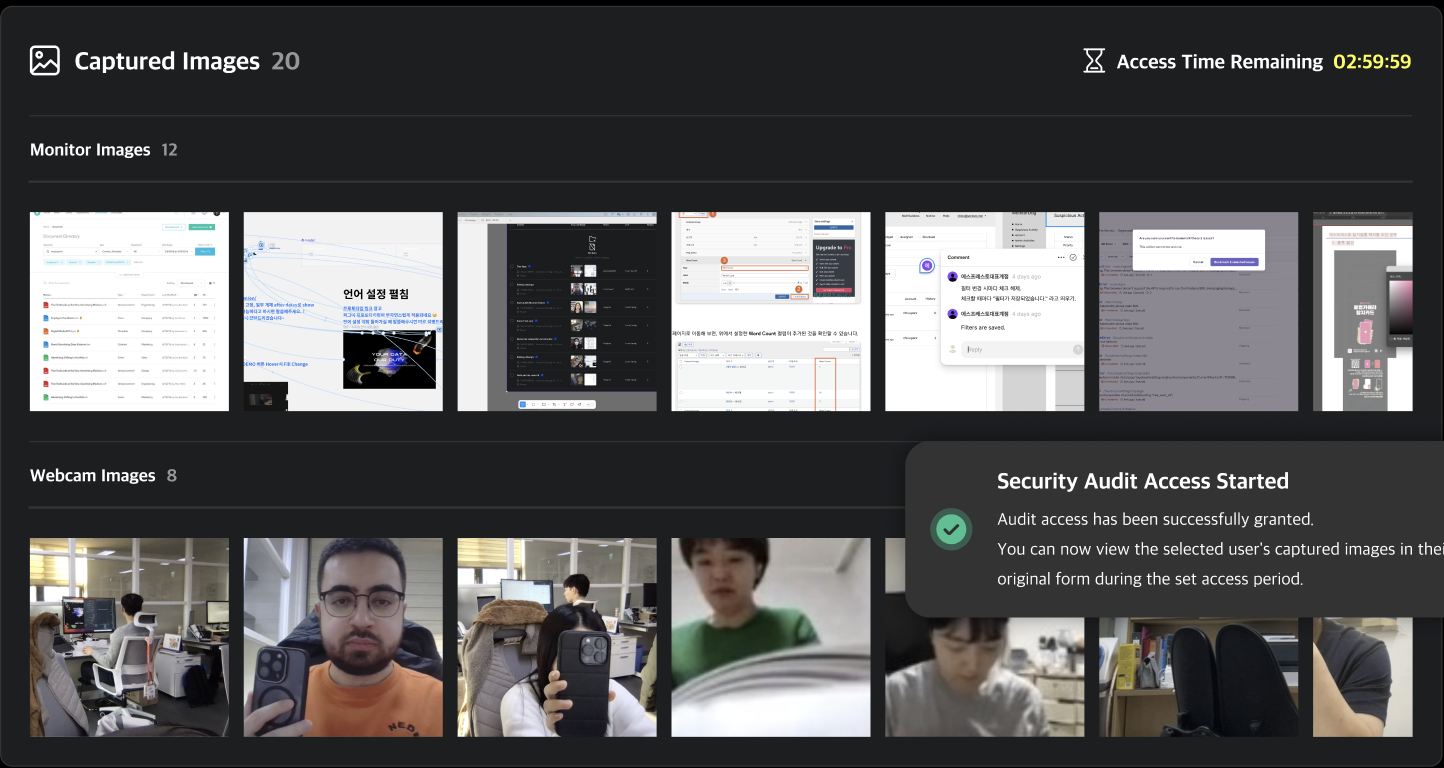
Once the audit begins, a countdown timer will appear at the top right based on the configured audit time, and the images will be made accessible. Any image viewed from the event detail page will be added to the security audit list, and you can review the events and images later via the security audit detail page.
Q. I can’t submit an audit request!
A. Only administrators with Viewer or higher permissions can submit a security audit request. If you want to view the images and proceed with the audit, please contact a higher-level administrator to request a permission change.
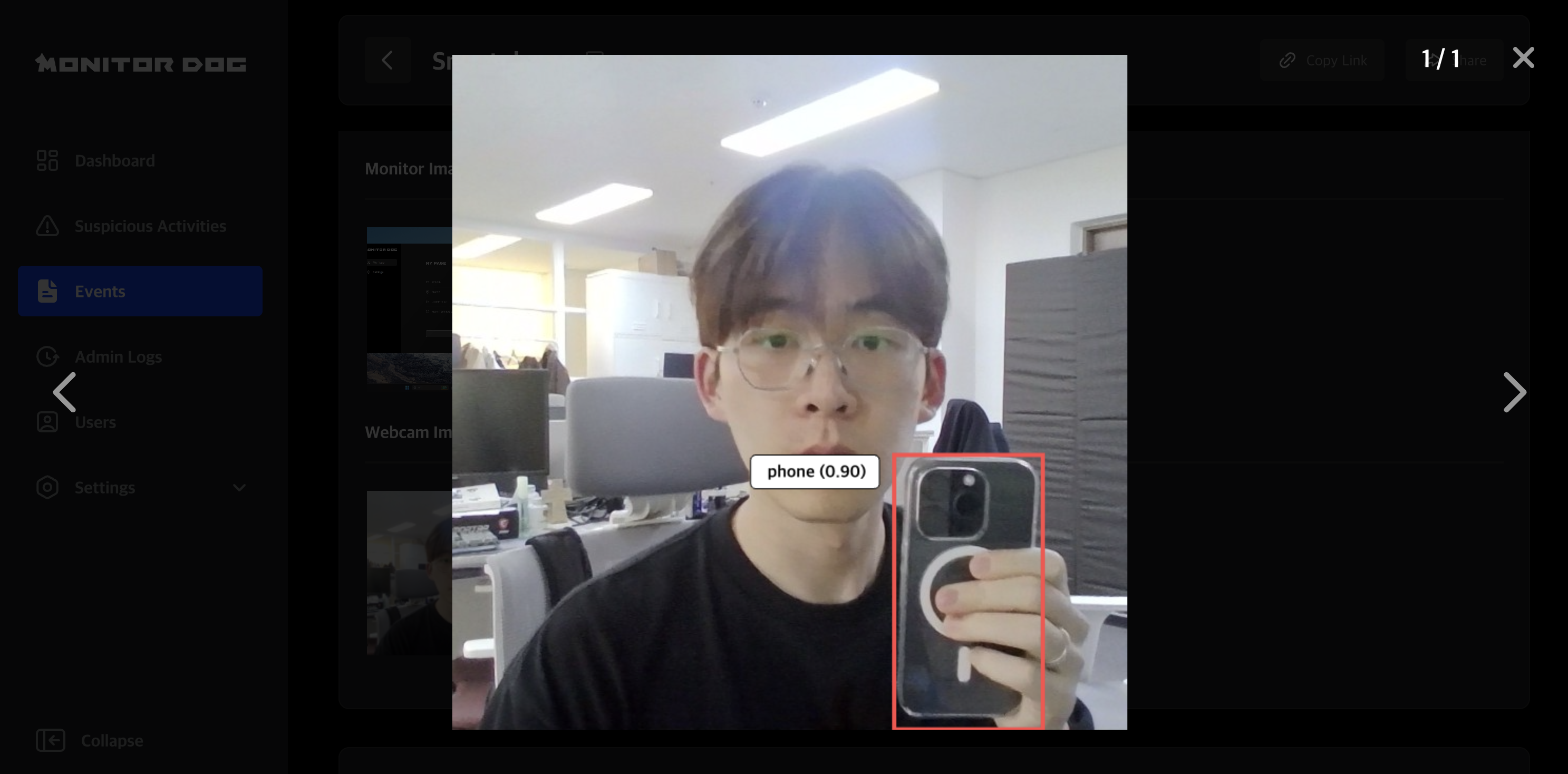
Smartphone Detection Events
Smartphone presence is automatically detected in webcam images using MonitorDog AI.
Click to view a large version showing risk levels and bounding boxes.
User Info
Displays data on the user who triggered the activity.
Click the user name to visit their detail page.
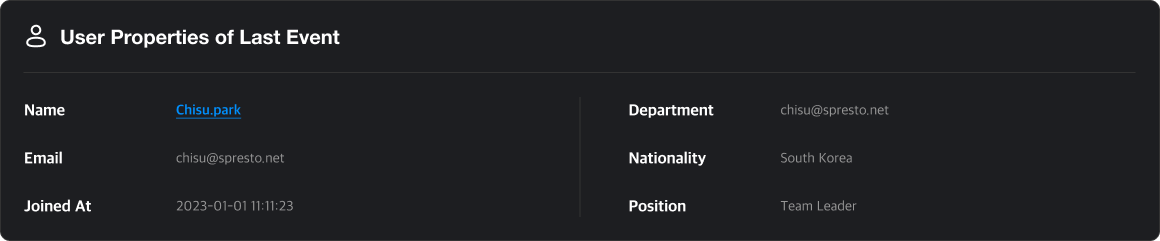
Q. How can I add department or nationality info?
A. Only administrators can add or modify this data.
You must have Editor-level access or higher to make changes.
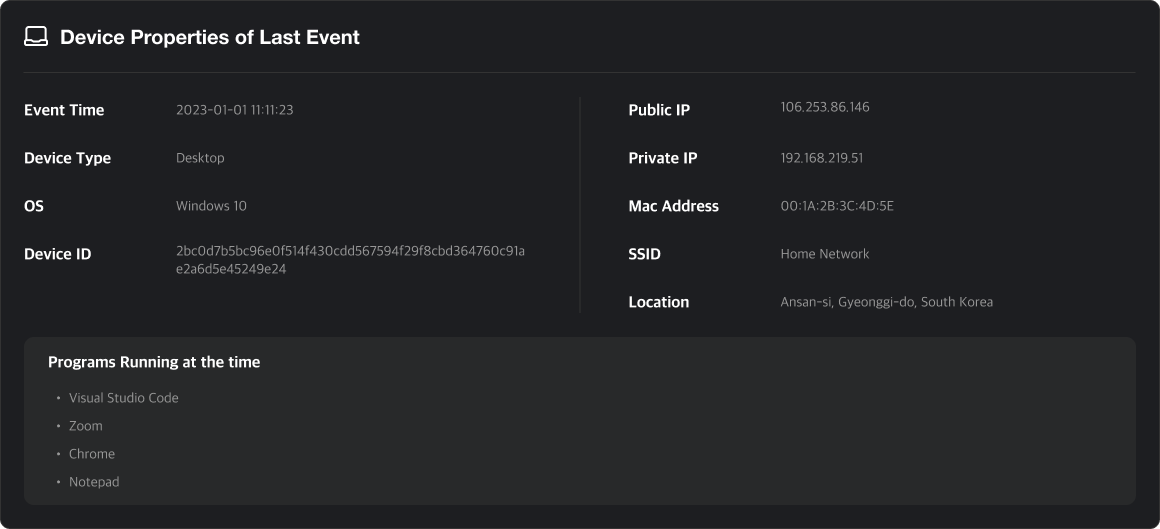
Device Info
Shows the device where the suspicious activity occurred and the programs that were running at the time.
This data is collected via the MonitorDog Agent.
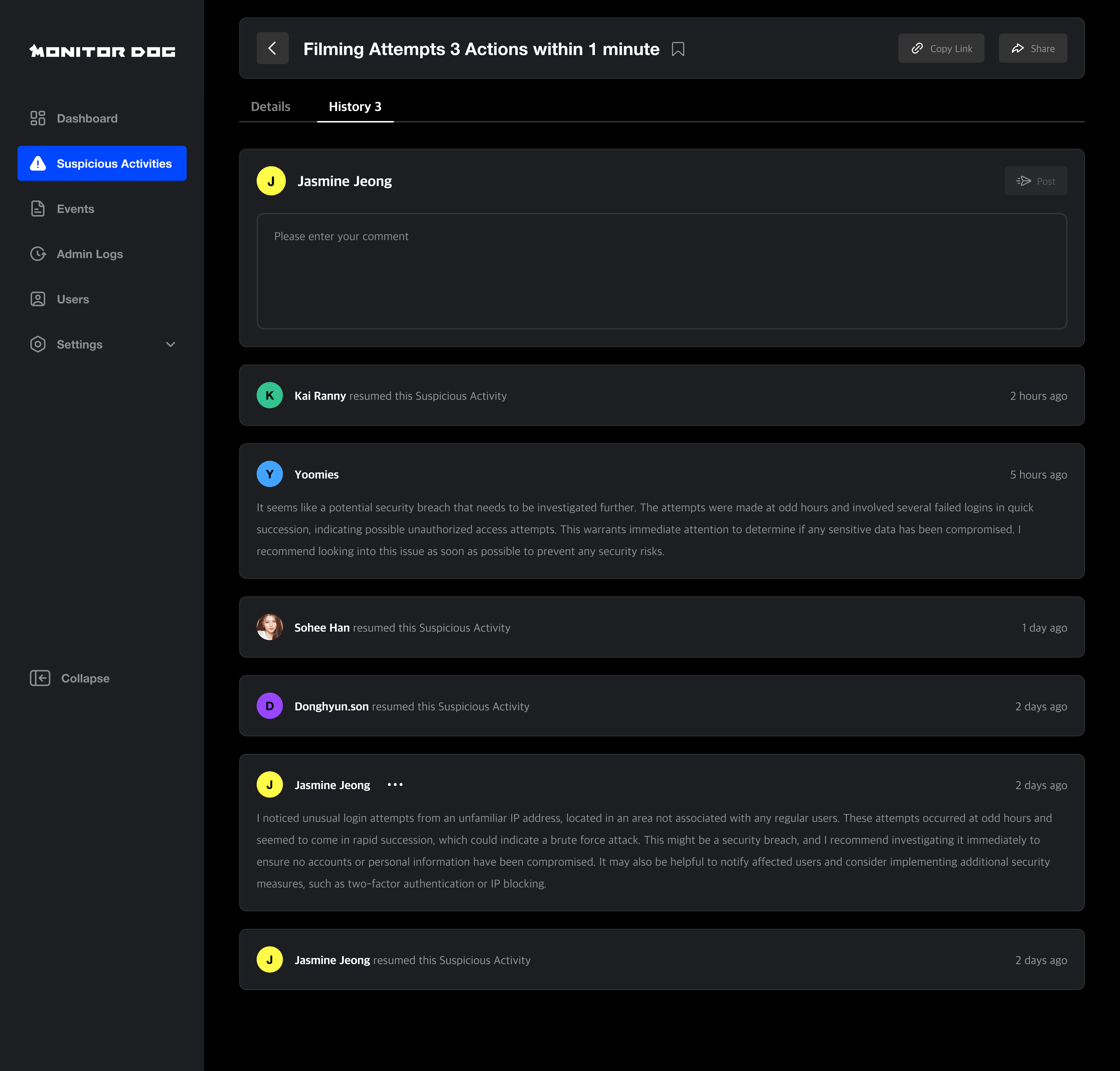
History
All admin actions and comments related to the activity are logged and viewable here.
Q. When is history generated?
A. History entries are added when:
- The review status or risk level is changed
- The item is shared with another admin
- A comment is left by an admin
Sharing
There are two ways to share a suspicious activity:
- Copy Link: Share via external means (e.g., message, email)
- Direct Share: Share with specific admins inside MonitorDog.
This sends a notification and creates a history entry.