MonitorDog Glossary
PC Agent
A desktop program installed on the user's computer that provides security functions to detect screen recording attempts and unauthorized access.
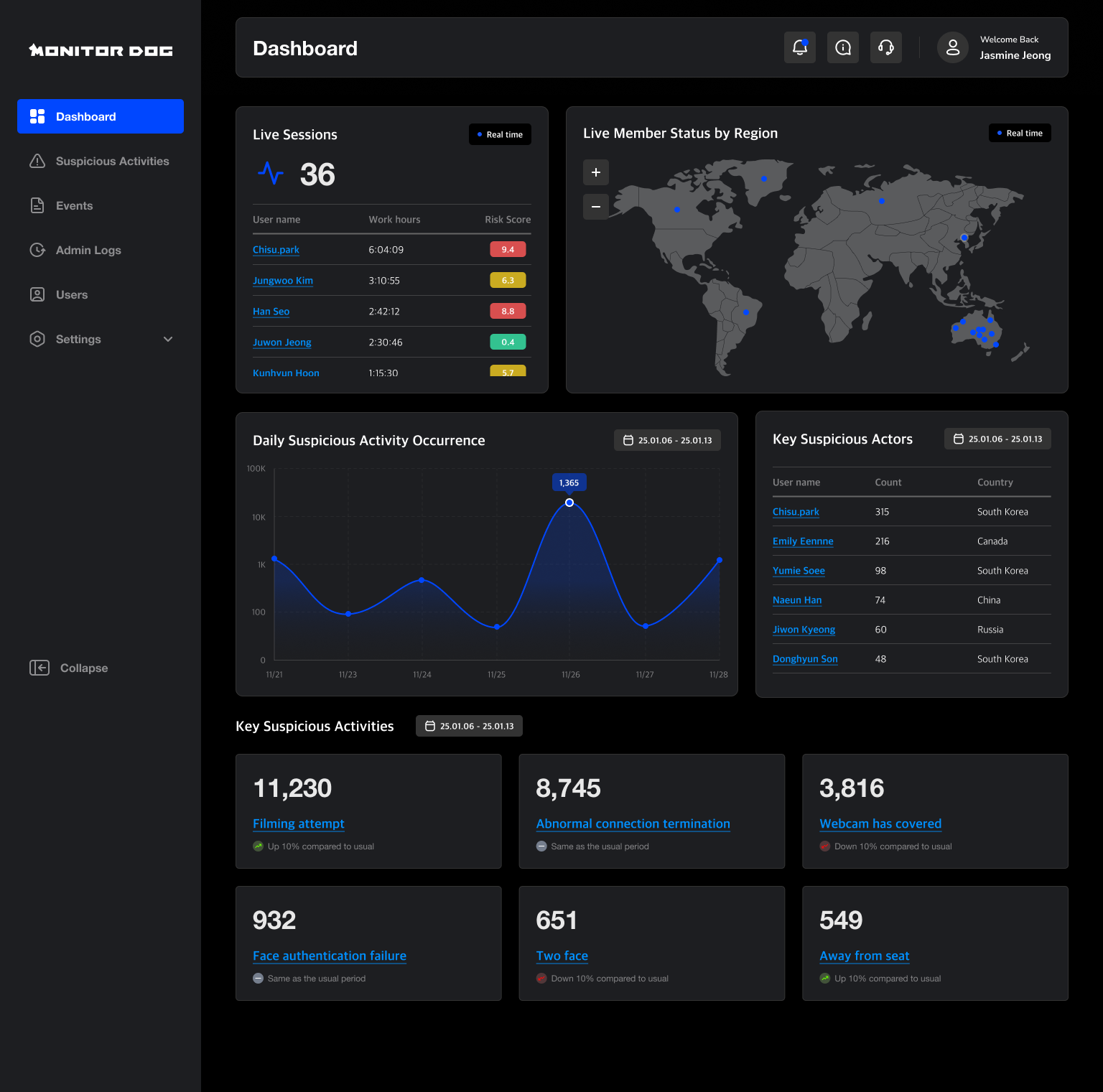
Admin Console
A web-based page for administrators, hosted either on the cloud or an internal server. It allows for policy configuration, agent control and status monitoring, and viewing of detection event logs.
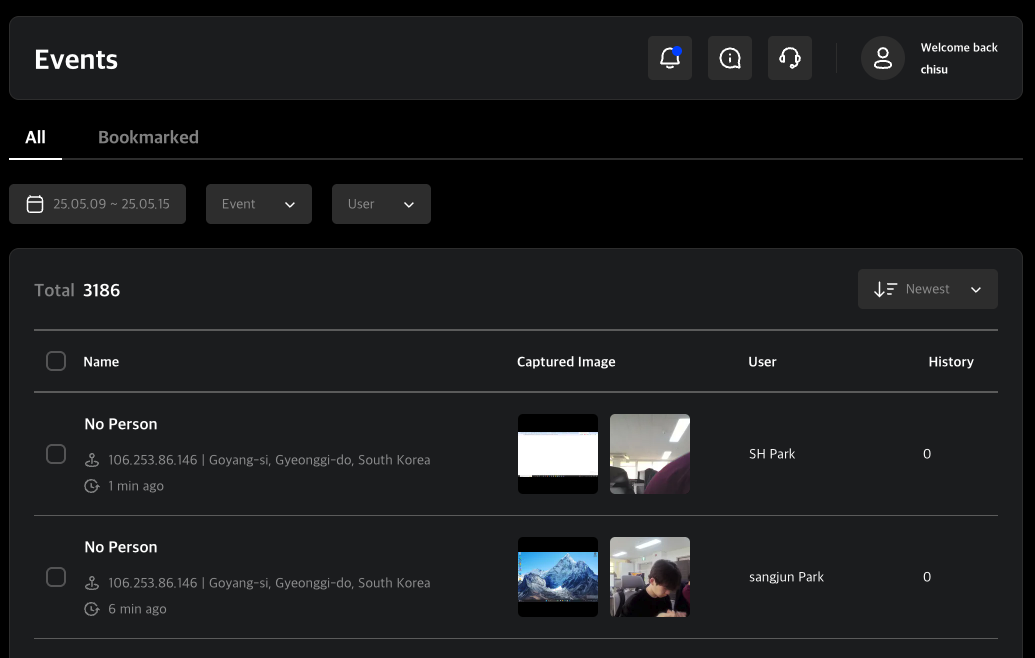
Event
An event is the smallest unit of data transmitted from the PC Agent to the server. Examples of events include:
- Suspicious behavior:
- Attempted screen capture
- User absence
- More than one person visible on screen
- Other abnormal behavior
- Face authentication success/failure
- Execution of suspicious programs
- Others
For example, when a user attempts to capture the screen, the PC Agent detects this and generates a "Screen Capture Attempt" event, which is then sent to the server. The server records the event, and the administrator can review it via the Admin Console.
MonitorDog does not treat events as suspicious behavior by default. However, based on the administrator's defined policies, specific events—or combinations thereof—can be treated as suspicious activities.
For instance, if a "Screen Capture Attempt" occurs too frequently within a short period (e.g., 10 times within 1 minute), these events may be grouped and classified as a single suspicious activity.
Refer to the following sections on Scenarios and Suspicious Activities for more information.
Scenario
A scenario is a customizable set of monitoring conditions defined by the administrator.
For example, if a scenario is configured to lock the device when there are more than 10 screen capture attempts within 1 minute, and such behavior is detected, MonitorDog will lock the device and generate a new Suspicious Activity.
Scenarios can be managed through the Admin Console, where they can be temporarily disabled, edited, or deleted as needed.
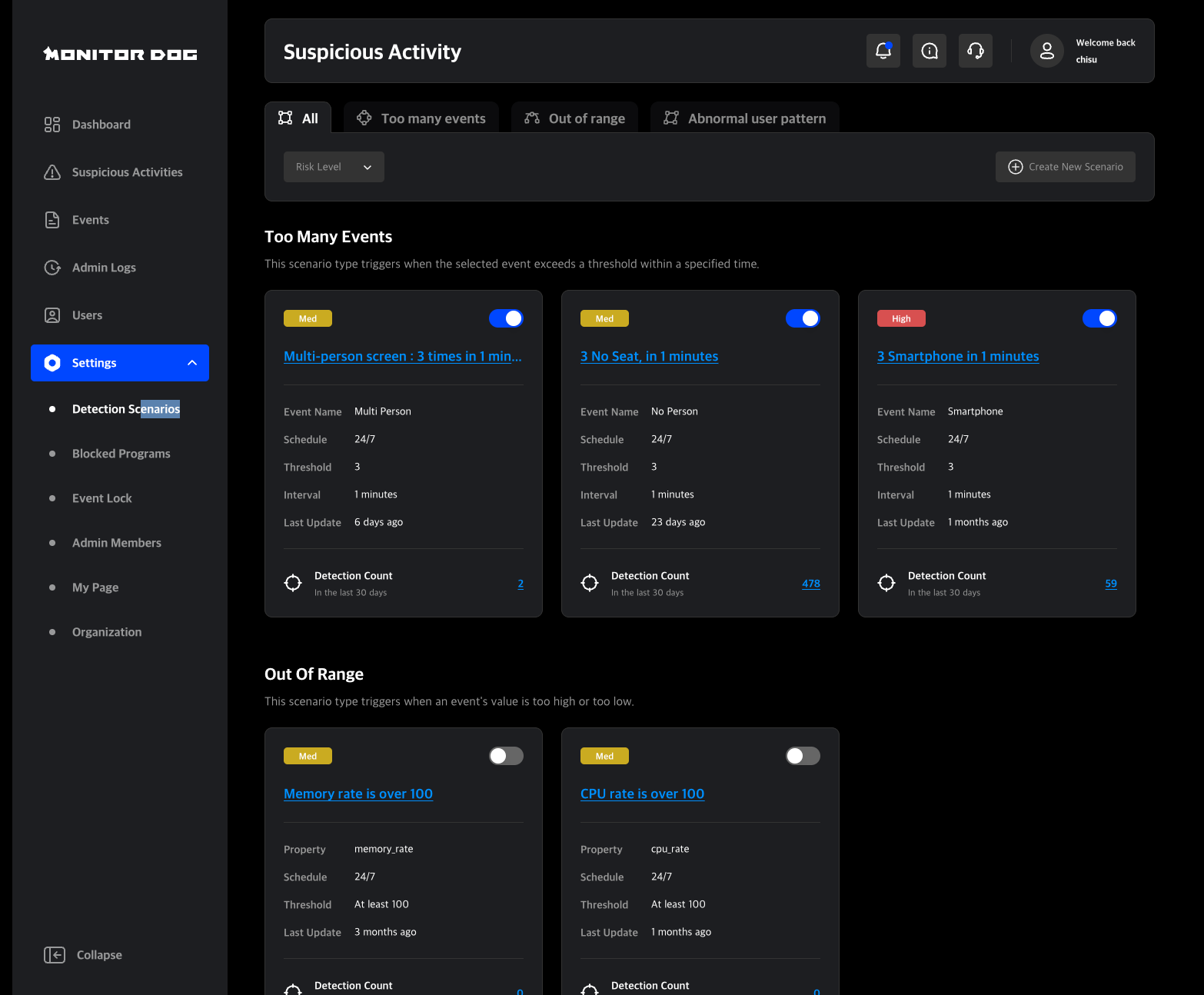
Suspicious Activity
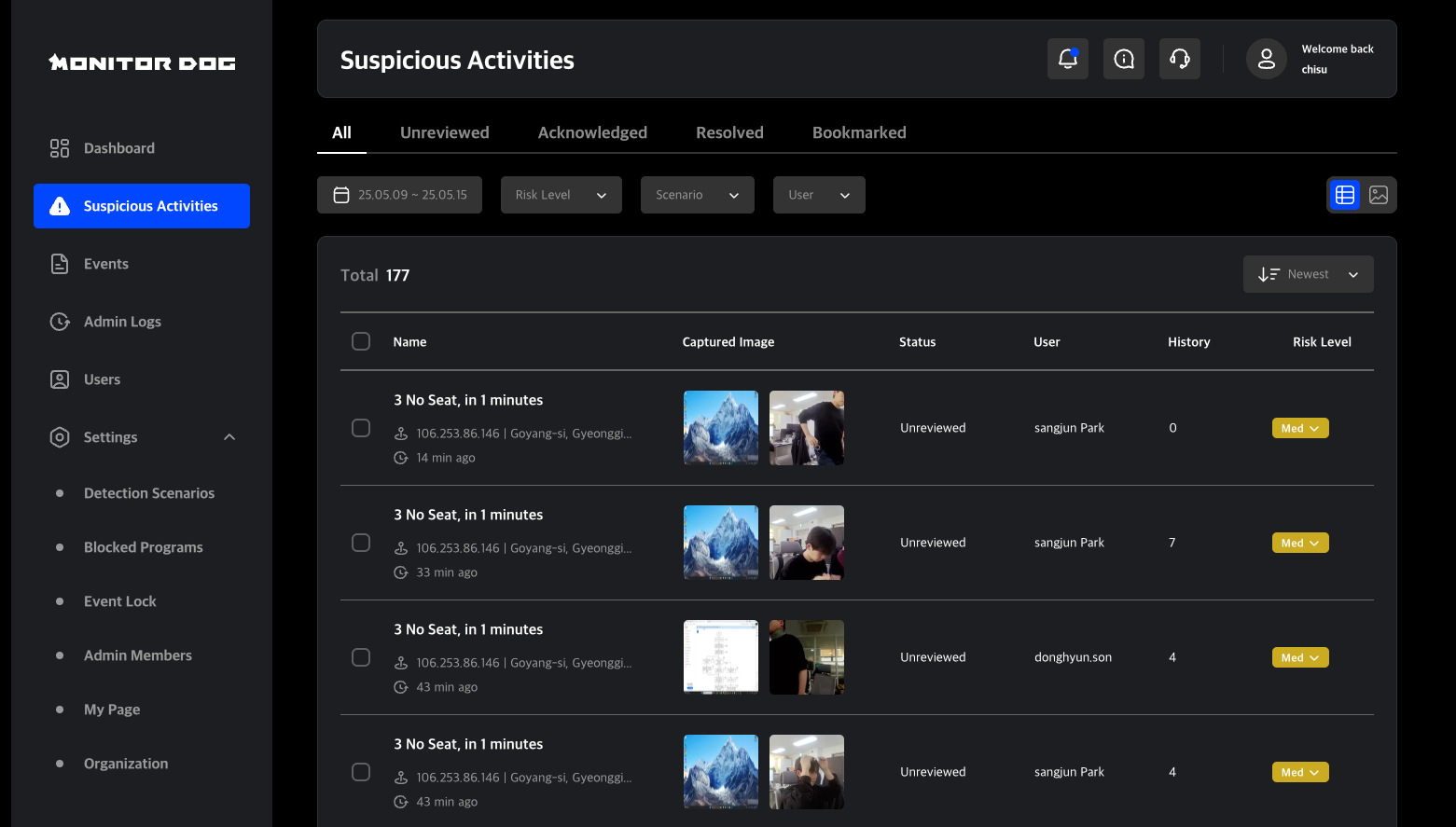
A suspicious activity is generated when certain events or a combination of them meet the conditions set in a scenario.
For example, if a user generates "Screen Capture Attempt" events repeatedly in a short span (e.g., 10 times in 1 minute), these may be grouped into a single suspicious activity.
Unlike individual events, suspicious activities are treated as high-priority alerts.
When a suspicious activity is detected:
- Admins may receive email notifications.
- Based on scenario settings, the user's PC may be automatically locked.
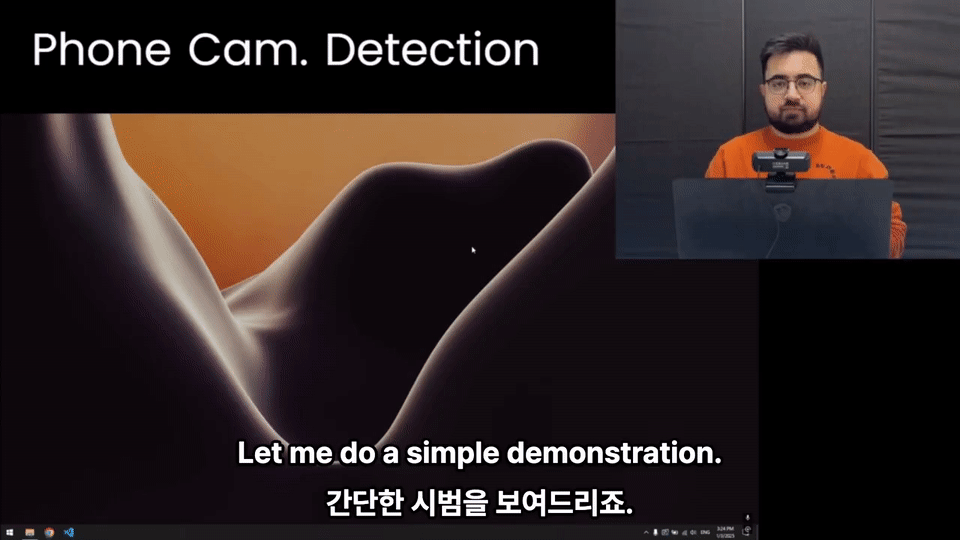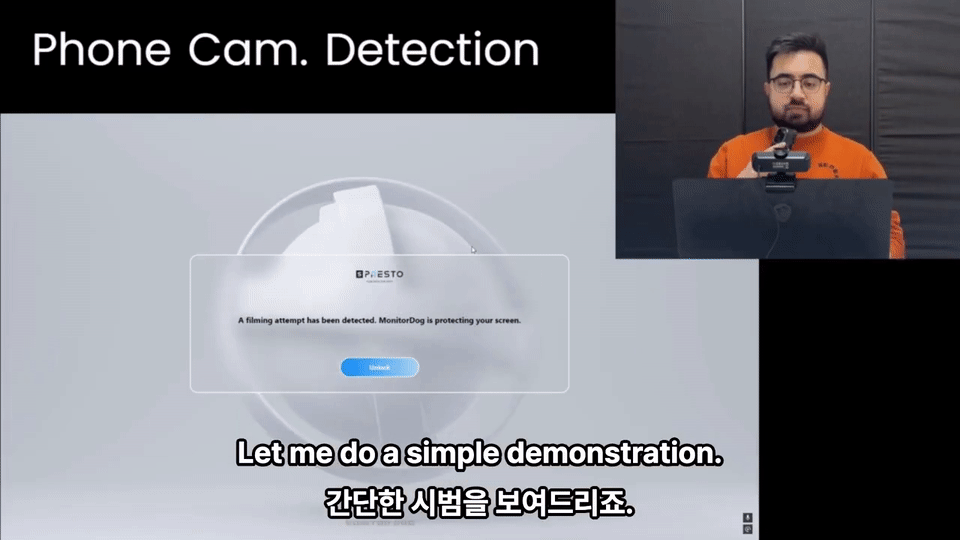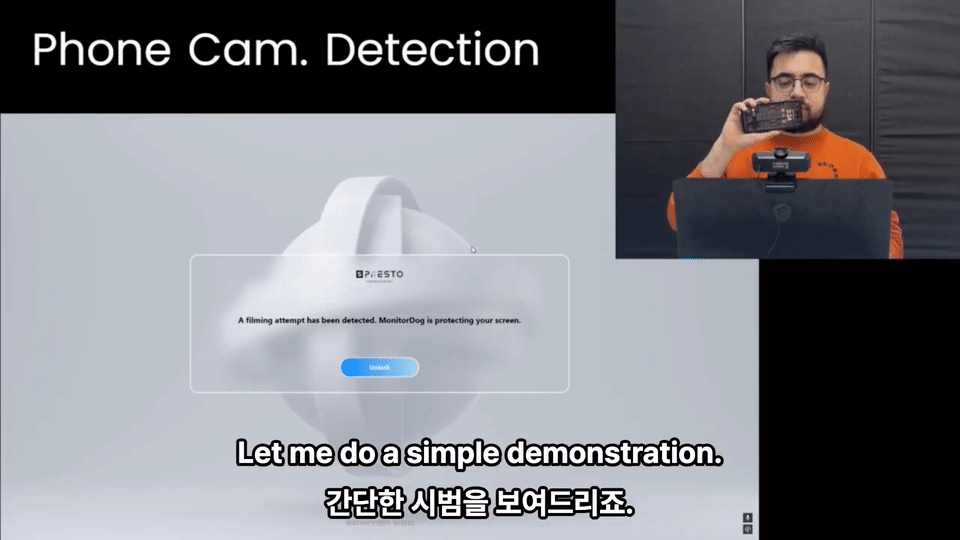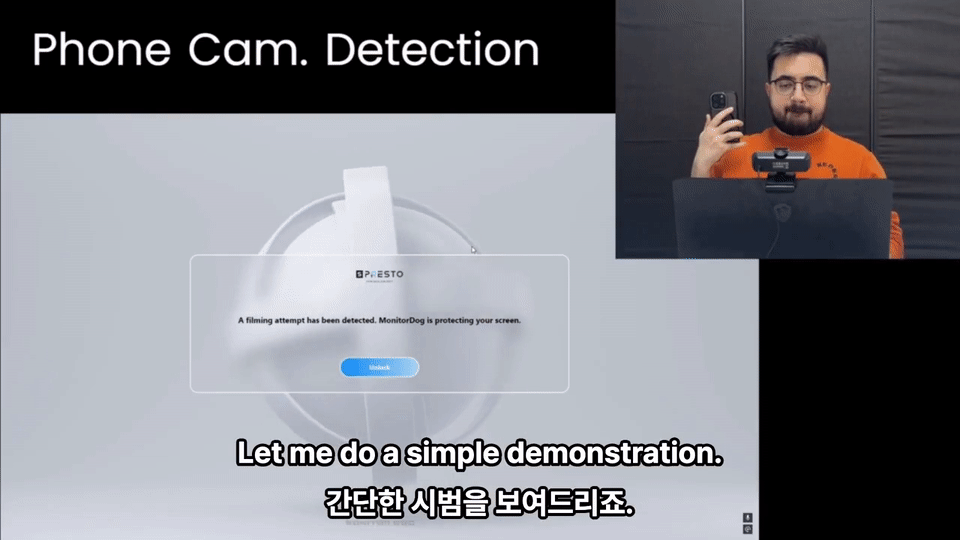
Lock
MonitorDog provides a lock function to immediately secure a PC during a critical incident and prevent data leakage. There are two types of lock mechanisms: Event Lock and Remote Lock.
Event Lock
An event lock is triggered automatically by the PC Agent when a suspicious event occurs, temporarily locking the PC to prevent further risk.
For example, if the user attempts to capture the screen:
- The Agent detects the attempt and creates a "Screen Capture Attempt" event.
- Based on the admin’s settings, this may immediately trigger an event lock.
The lock will automatically be lifted after a certain duration if the suspicious condition no longer persists.
Example: Screen capture attempt → Event lock → Reassess after N seconds → Auto-unlock if no further issues
Event Lock applies only to specific webcam events (e.g., smartphone detection, user absence). The Admin Console allows setting which events trigger locks and for how long.
Remote Lock
A remote lock allows administrators to manually lock a user’s PC from the Admin Console.
Admins can select a user and click “Lock User” to execute the command. Remote locks can also be triggered automatically when a suspicious activity is detected, based on scenario settings.
The PC remains locked until manually unlocked by the admin or the user (if authorized).
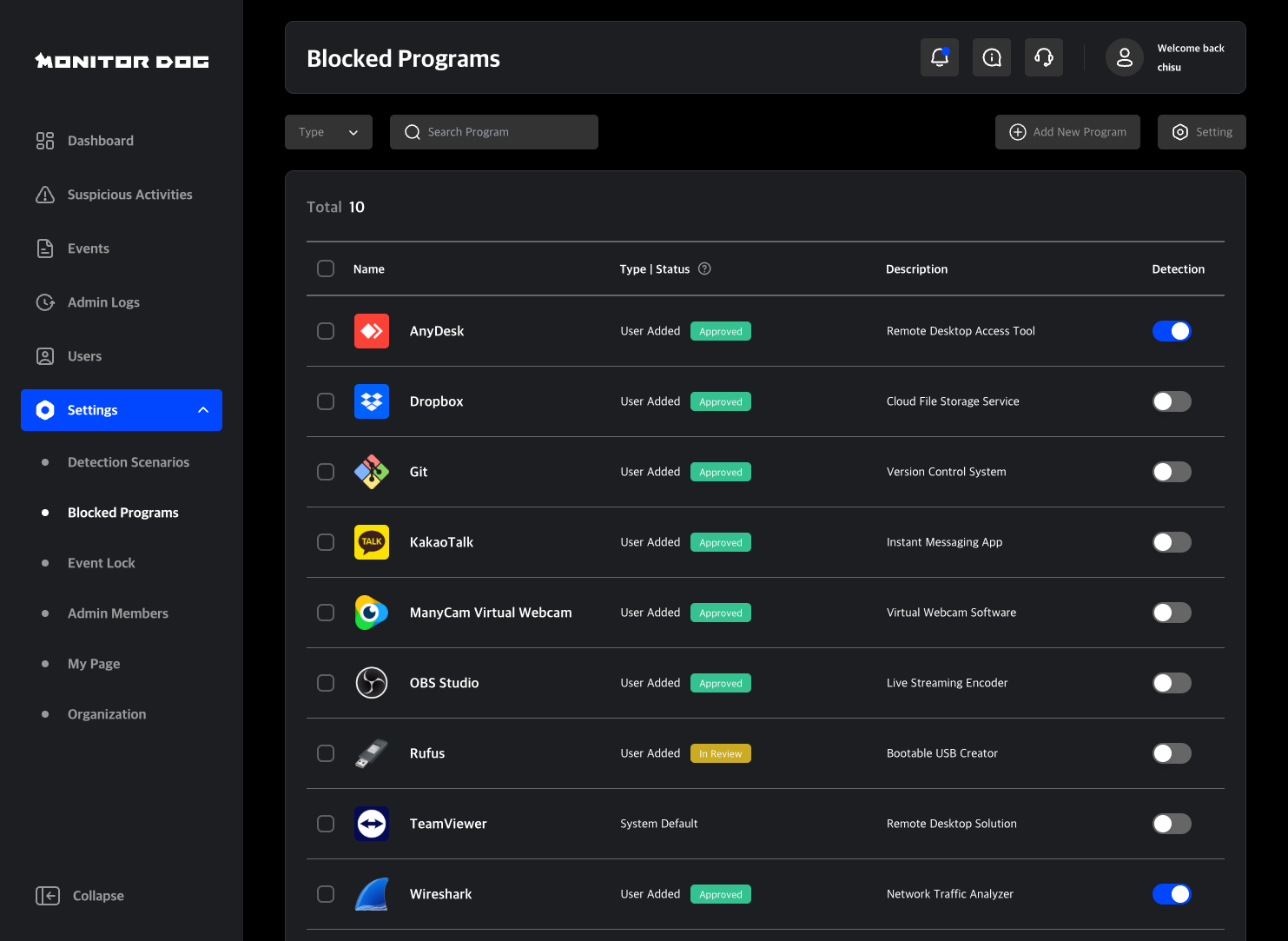
Blocked Programs
MonitorDog allows administrators to define a list of blocked programs. If a user attempts to launch a blocked application, the Agent will:
- Detect it
- Lock the screen
- Terminate the unauthorized program
For example, if KakaoTalk is registered as a blocked program, and the user opens it, MonitorDog will lock the PC and force-close KakaoTalk.
Program registration is done in the Admin Console, but it is not enforced immediately.
Once registered, a program enters an "In Review" state. After approval by the MonitorDog team, its status changes to "Approved" and monitoring begins.
The blocked program list is manageable via the Admin Console, where items can also be temporarily disabled, edited, or removed.
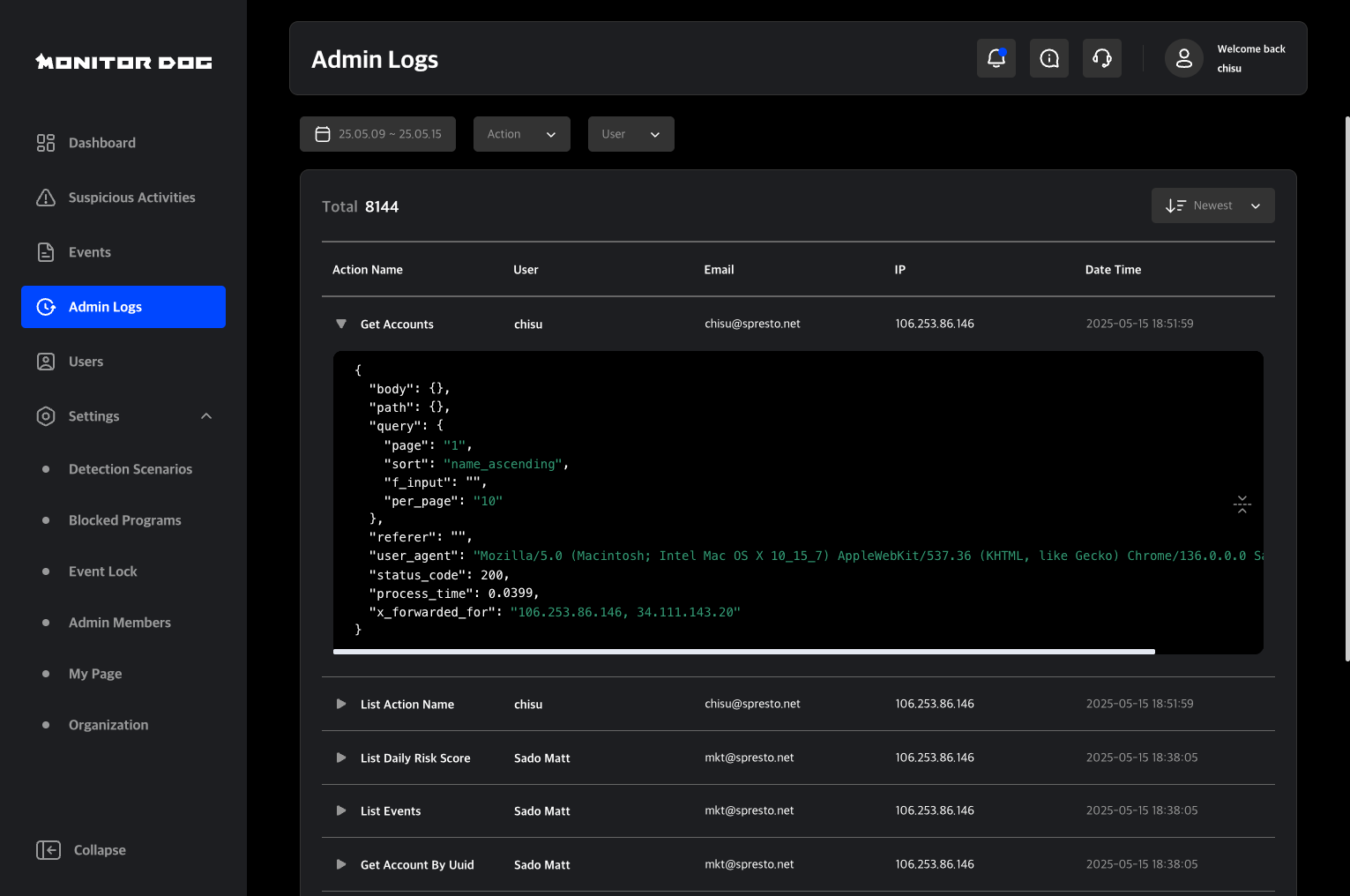
Admin Log
The Admin Log records all actions performed by administrators within the Admin Console.
For example, actions such as locking a user or registering a blocked program will be logged for auditing and traceability.
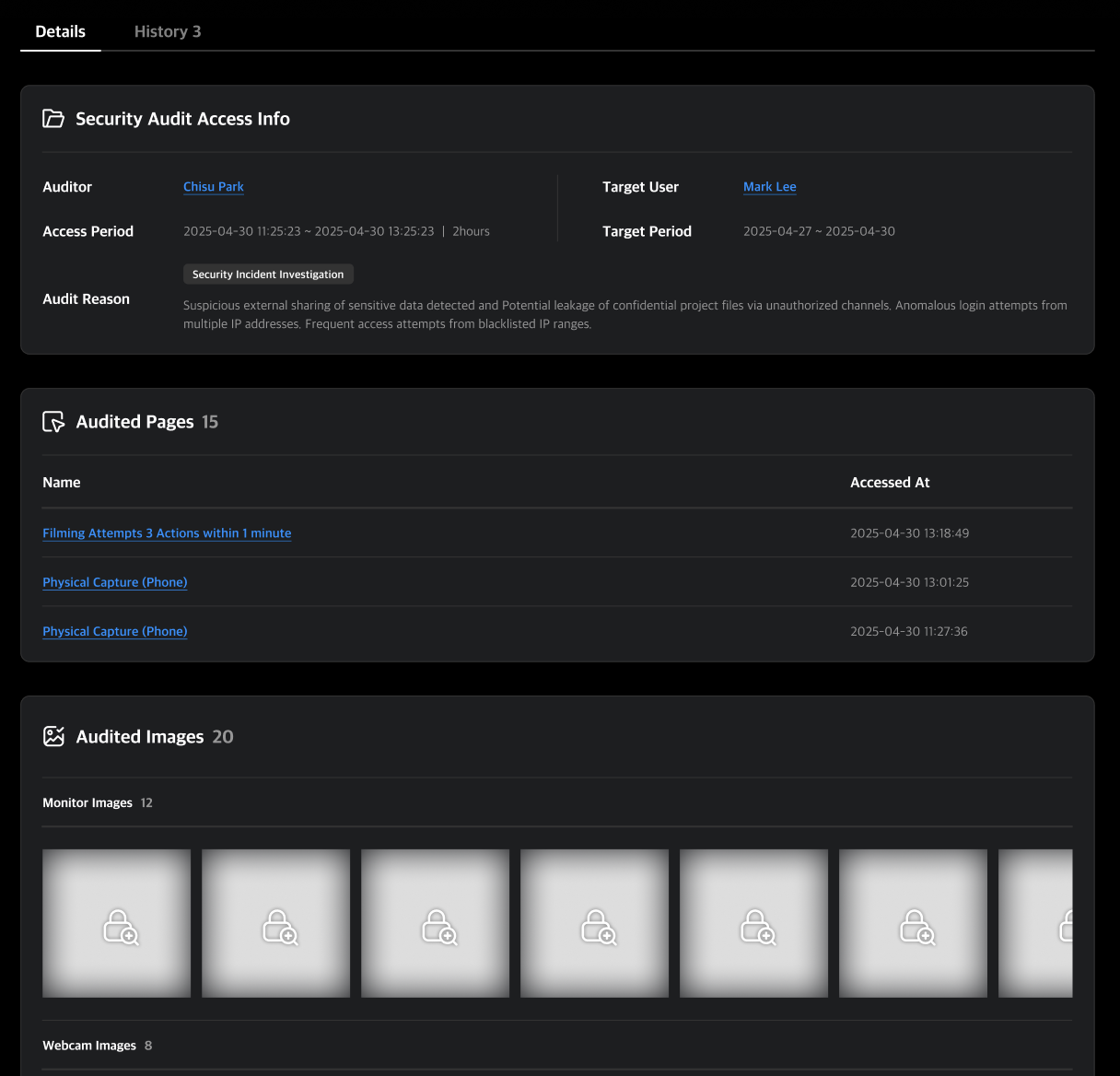
Security Audit
A security audit is a process initiated when an administrator needs to review event images associated with a specific user. To protect personal information and prevent data exposure, MonitorDog sets all images to private by default.
When a security audit is requested, a notification email is sent to the user under audit, and only the requesting administrator is granted access to event images that occurred during the specified period. Once the audit duration expires, the images are automatically set back to private.